Information Technology Reference
In-Depth Information
Figure 9. Traffic vs. query range (ε)
summarY and perspectIves
We have presented the most significant trends in
recent research in the field of content based music
information retrieval in peer-to-peer networks.
Despite the diminished attention the area has
received in general terms, its relatively close area
of metadata MIR in P2P is by far new. On the
contrary, it could be argued that it was actually
one of the key threads that lead to the widespread
acceptance of P2P systems.
Though, as metadata prove to be inefficient for
the purposes of MIR as well as the peculiarities of
music in comparison to text and image data, the de-
velopment of dedicated solutions for CBMIR in P2P
networks becomes obvious. As described, CBMIR
in P2P networks presents unique challenges.
P2P networks can be classified according to
numerous of their characteristics. A number of
prominent research works have been presented in
this chapter falling within all categories. Despite
an obvious tendency towards decentralized un-
structured models, solutions for other categories
of P2P models do exist. Additionally, we have
presented an initial attempt of CBMIR to invade
the area of wireless P2P networks, as well as the
challenges presented in that case.
The prospects of MIR in P2P networks, both
in terms of research and applications, seem to be
encouraging. As it is relatively new a research
field, it contains several open research issues. Fol-
lowing ethics, a very important area of possible
further development is the implementation of data
rights management. As the previously mentioned
widespread penetration of P2P systems based
on the illegal exchange of copyrighted material,
methods are required to enforce rights on data.
Another field is music e-commerce. Attempts like
iTune or iMusic changed the paradigm that music
is merchandised. Moreover, applications in P2P
environments (such as Napster and Kazaa) can
only set the path for commercial CBMIR in P2P
networks. Additionally, with the development of
high CPU capability mobile computing devices,
Figure 10. Traffic & number of results vs. CMF
Figure 9 shows the results for traffic with respect
to
ε
. CM, LC, and GC perform similarly, thus
only the results for the former are included. As
ε increases, more results are found and, conse-
quently, backward traffic increases too (forward
traffic is unaffected). However, the increase is
much more obvious for ML, whereas CM, due
the effectiveness of the policy for the backward
phase, has a very smooth increase.
The last experiment, examines the sensitivity
of CM against
CMF
. The traffic and number of re-
sults of CM, for varying
CMF
values, are depicted
in Figure 10. When
CMF
is high, the effectiveness
of the policy for the backward phase is limited,
since most MHs are selected at random by this
policy, resulting to high backward traffic.
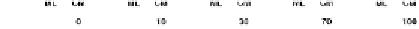

















Search WWH ::

Custom Search