Information Technology Reference
In-Depth Information
Table 2. Key components of DRM
Component
Short description
• Controls who has access to the content and how it is used.
• Technologies used are encryption (e.g., symmetric, asymmetric), passwords, and copy protection systems.
Access and Usage Control
• Protects the authenticity and integrity of the digital content. Integrity: securing that the object has not
be changed or altered. Authenticity: securing that the object is an object which claims to be.
• Different types of objects exist such as digital content, rights owner, and user.
• Technologies used are watermarks and digital signature.
Protection of Authentic-
ity and Integrity
• Allows the identification of a digital content by metadata.
• Different types of objects exist such as digital content, rights owner, and user.
• Different identification mechanisms are used. Metadata can be a part of the digital content or be added
to the digital content.
Identification by Metadata
• Includes all hardware and software used by the end-device where the digital content is being played,
viewed, or printed.
• For hardware this could be a personal computer, laptop, or a PDA. For software this might be the Windows
Media Player or Real Player.
Specific Hardware and
Software for End-Devices
• Search engines which search the network for illegal copies of digital content, integrity of digital content,
or user registration.
• Technologies used are search engines looking for watermarks or digital fingerprints.
Copy Detection Systems
• Billing systems should be able to handle different pricing models such as pay per use, monthly subscription.
• Different types of billing systems. From Monthly billing, credit card systems (Secure Electronic Transac-
tion Systems), electronic payment systems, or micro-payment systems.
Billing Systems
• DRM systems must as well include systems, which support contract negotiation, accounting information
and all other sort of information.
• Different standards exist such as Electronic Data Interchange (EDI) or extensible Markup Language
(XML) -based systems.
Integrated E-Commerce
Systems
are the permissions, constraints, and obligations
that are granted to or placed on the user and which
they apply to the content.
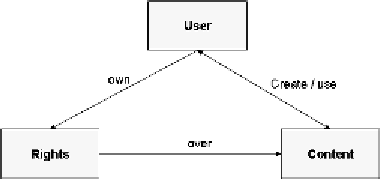
As Figure 3 shows, the content is created by
an entity called the user. Either the user also uses
this content, or the content is used by another
user. The creator of the content, which can also
use the content, owns certain rights that can be
exercised over the content.
At the core of any DRM is the rights model.
It describes the type of rights as well as their at-
tributes/constraints associated with these rights.
There are three sets of rights. First, render rights
including the right to print, view, and play. Sec-
ond, transport rights including the rights to copy,
move or loan the digital content from one place or
device to another. Finally derivative work rights
including the right to extract, edit, augments, or
embed the digital content. It deals with all kind
of manipulations of digital content.
Another important part of the rights model are
the rights attributes. They change relative to each
of the three main rights. For example, an attribute
of a render right might be the type of devices on
which the content can be played (e.g., a computer
Figure 3. Core entities in DRM











Search WWH ::

Custom Search