Information Technology Reference
In-Depth Information
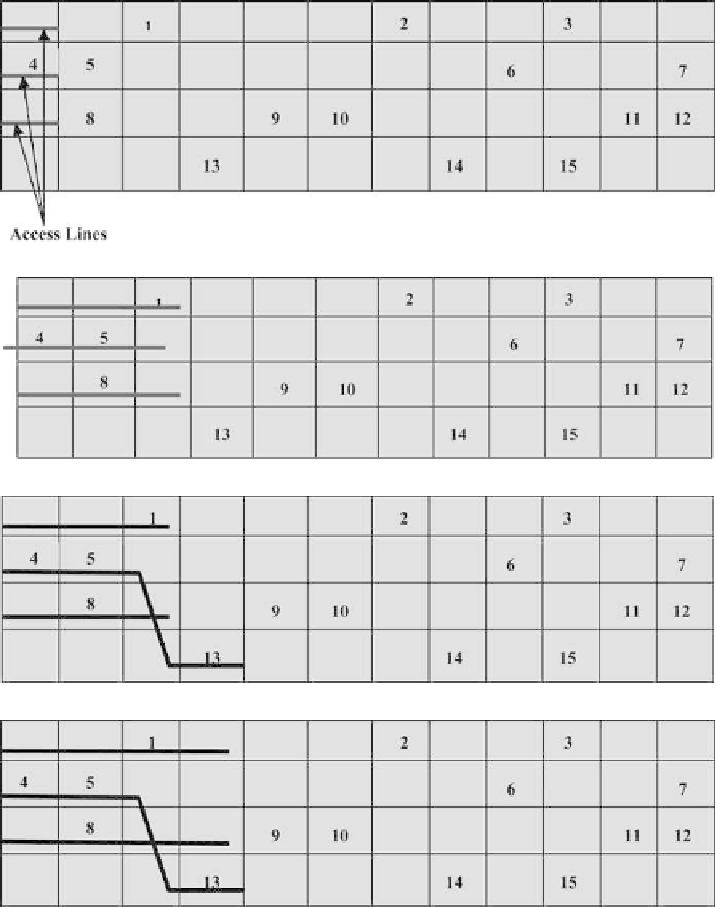
(a)
(b)
(c)
(d)
F
IG
. 40. A running example of the POS algorithm. (a) Access lines are initialized (7). (b) Extending
the access lines without channel switching (11-12, 17-18). (c) Moving to the right and an inside switch
(13-16). (d) Advancing the access lines without any inside switch (17-18). (e) Generation of the final
access lines.