Information Technology Reference
In-Depth Information
F
IG
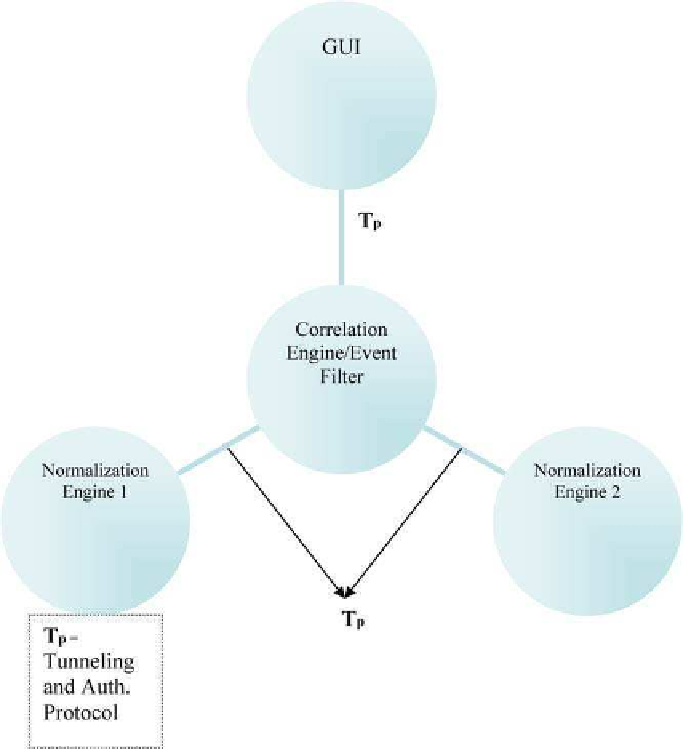
. 6. Correlating normalized events.
3.6.2
Interpretation of Log Files
In most cases the security administrator reads the result of a correlation done by a
certain tool, but he only sees the tip of the iceberg. If you look at the figures in this
chapter, the set of processes upstream of the GUI display is much more complex.
Whatever the case may be, the literature indicates two basic methods for analyzing
logs, called
approaches
.