Information Technology Reference
In-Depth Information
3 . 5
N o r m a l i z a t i o n a n d D a t a R e d u c t i o n : P r o b l e m s a n d
P o s s i b l e S o l u t i o n s
Normalization is identified in certain cases with the term
event unification
. There is
a physiological need for normalization in distributed architectures. Numerous com-
mercial systems prefer the use of XML for normalization operations. This language
provides numerous opportunities for event unification and management of digital
signatures and hashing. There are two basic types of logs: system logs and network
logs. If the reports all had a single format there would be no need for normalization.
In heterogeneous architectures it is obvious that that is not the case. Let us imagine,
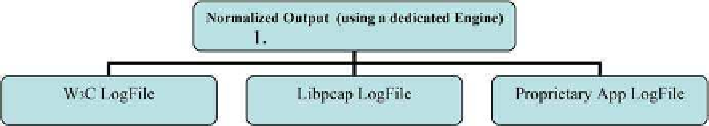
for example, an architecture in which we have to correlate events recorded by a web-
site, by a network sniffer and by a proprietary application. The website will record
the events in w3c format, the network sniffer in LibPcap format, while the propri-
etary application might record the events in a non-standard format. It is clear that
unification is necessary here. The solution in this case consists of finding points in
common among the various formats involved in the transaction and creating a level
of abstraction according to the diagram in
Fig. 4
.
It follows in this case that an attacker can once again seek to violate log integrity
by zeroing in on the links between the various acquisition points and the point of
normalization. We will discuss this below. Regarding the correlation, the point of
normalization (normally an engine) and the point of correlation (an activity that may
be carried out by the same module, for example, in an IDS) may be the same ma-
chine. It is clear that this becomes a potential point of failure from the perspective
of network forensics and thus must be managed both to guarantee integrity and to
limit possible losses of data during the process of normalization. For this purpose
the state-of-the-art is to use MD5 and SHA-1 to ensure integrity and to perform an
in-depth verification of the event unification engine to respond to the data reduction
issue, keeping the “source” logs in the normalized format. In
Fig. 5
, where each
source log is memorized on ad hoc supports, another layer is added to
Fig. 4
.
In order to manage the secure repository section and still use a series of “source
log files” that guarantee a certain reliability, the machines in the second line of
Fig. 5
F
IG
. 4. Normalization.