Information Technology Reference
In-Depth Information
F
IG
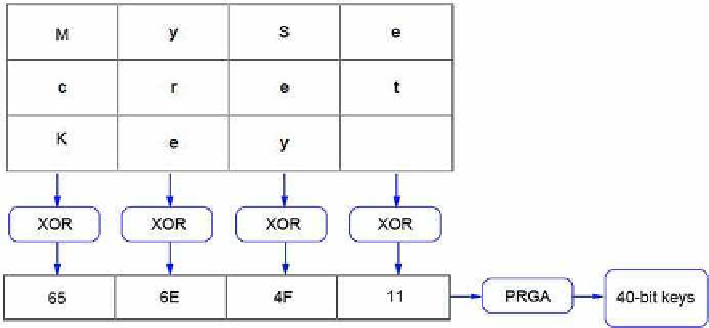
. 3. XOR operation performed by the Neesus DataCom key generation algorithm.
each word in the dictionary is treated as the WEP key. WEPAttack uses the IV that is
found in the encrypted data packet and prepends it to the words in the dictionary. This
key is used to find the cipherstream which is XORed against the encrypted packet.
If the decrypted packet starts with 0xAA (the standard SNAP header value), there is
a good chance that the key has been found. More than one encrypted packet should
be used for the processes since not all packets start with 0xAA. However, the chance
that two packets, picked at random, are neither IP nor ARP (both start with 0xAA) is
very unlikely.
2 . 3 T h e F M S A t t a c k
The FMS attack is the most well known attack on WEP. It is derived from (and
named after) Scott Fluhrer, Itsik Mantin, and Adi Shamir who published their re-
search findings in a 2001 paper entitled “Weaknesses in the Key Scheduling Algo-
rithm of RC4”
[5]
. The basis for this attack is a weakness in the way RC4 generates
the keystream. Specifically:
1. The Initialization Vector (IV) that is always prepended to the key prior to the
generation of the keystream by the RC4 algorithm is transmitted in cleartext.
2. The IV is relatively small (three bytes) which results in a lot of repetitions as
the relatively small (16.78 million) number of unique IVs are re-used to encrypt
of packets.
3. Some of the IVs are “weak” in the sense that they may be used to betray infor-
mation about the key.