Information Technology Reference
In-Depth Information
8.6 Performance Evaluation
In this section, we use a trace-driven simulator written in ns-2 [12] to evaluate the performance
of the presented adaptation algorithm (denoted by AVS) and compare it with the current state-
of-the-art algorithm proposed by Cuetos and Ross [1-2] (denoted by CR).
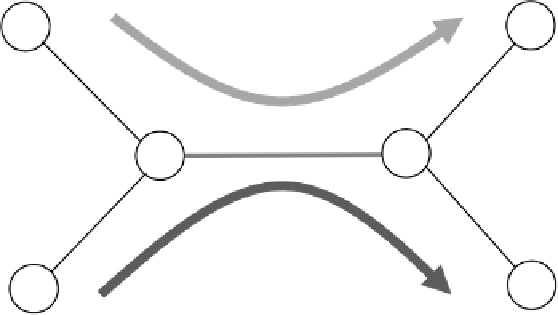
Figure 8.4 depicts the simulated network topology. We use the common NewReno TCP [13-
14] as the transport protocol to deliver the video data to the client. Cross-traffic is generated
from a packet trace file obtained from Bell Labs [15-16].
1
The trace file captured 94 hours of
network traffic passing through a firewall. We divide the 94-hour trace file into 94 1-hour trace
files and run a simulation for each 1-hour trace file to evaluate the algorithms' performance
under different cross-traffic scenarios.
Both the streaming traffic and the cross-traffic share a link of
R
Mbps as shown in Fig-
ure 8.4. For each simulation, we adjust
R
so that the network has just sufficient bandwidth to
stream the video, i.e.,
R
c
, where
c
is the average data rate of the cross traffic. We
summarize the system settings in Table 8.1.
We use two performance metrics, namely, rebuffering ratio and average video bit-rate, to
evaluate the algorithms' performance. Rebuffering ratio is defined as the proportion of frames
=
r
max
+
Streaming Client
Streaming Server
Video Stream
R
Mbps, 100ms
Cross -Traffic
Avg_rate =
c
Cross-Traffic Generator
Cross-Traffic Receiver
Figure 8.4
Network topology used in simulations
Table 8.1
System parameters used in simulations
Parameters
Value
Prefetch duration
5 seconds
M
1 second
r
max
1.1 Mbps
r
min
200 kbps
Video Length
3000 seconds
TCP MSS
1500 bytes












Search WWH ::

Custom Search