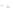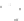Information Technology Reference
In-Depth Information
Fig. 3.3
A Simpli fi ed Illustration of Public Key Encryption
Given these keys, two things can be accomplished. First, the protected health
information can be secured so only the intended recipient can view it. This is because
a message encrypted (“scrambled”) with the
intended recipient's public key
cannot
be decrypted (“unscrambled”) by anyone unless they possess the matching private
key so, presumably,
only the intended recipient
can open it. It is important to note
that compromise of the recipient's private key defeats this. This could happen if
malware infected a computer where the key is stored and stole it.
Trust
: In addition to encrypting the data so only the intended recipient can read it,
public key encryption can help make sure that the person who sent the message is
who they say they are. This is done by also sending a “digital signature”, an associ-
ated message encrypted with the
sender's private key
. Assuming only the sender has
this private key, then when anyone opens the digital signature using the
sender's
public key
they have proof of who sent the message.
Fig. 3.3
summarizes the two important capabilities of Public Key Encryption we
just discussed. As with many of the illustrations, it intentionally avoids some techni-
cal details in the interest of clarity. For example, in a health system, a more complex
infrastructure might well be in place.
An associated issue is how to make certain that a public key is correct and belongs
to the claimed person or entity. The usual solution is a public-key infrastructure
(PKI), in which one or more third parties, known as certificate authorities, certify
ownership of key pairs. PKI allows entities to trust that the public key they are using