Information Technology Reference
In-Depth Information
DPM requires that an agent be installed if it is going to be configured to protect a computer.
The agent identifies which data on the computer can be protected, tracks changes that oc-
cur to that data, and manages the process of forwarding protected data from the protected
computer to the DPM server. You need to configure any firewall on the DPM server to allow
inbound TCP port 135 traffic, as well as allowing traffic to the DPM service (msdpm.exe) and
the protection agent (dpmra.exe).
To deploy the DPM agents, perform the following steps:
1.
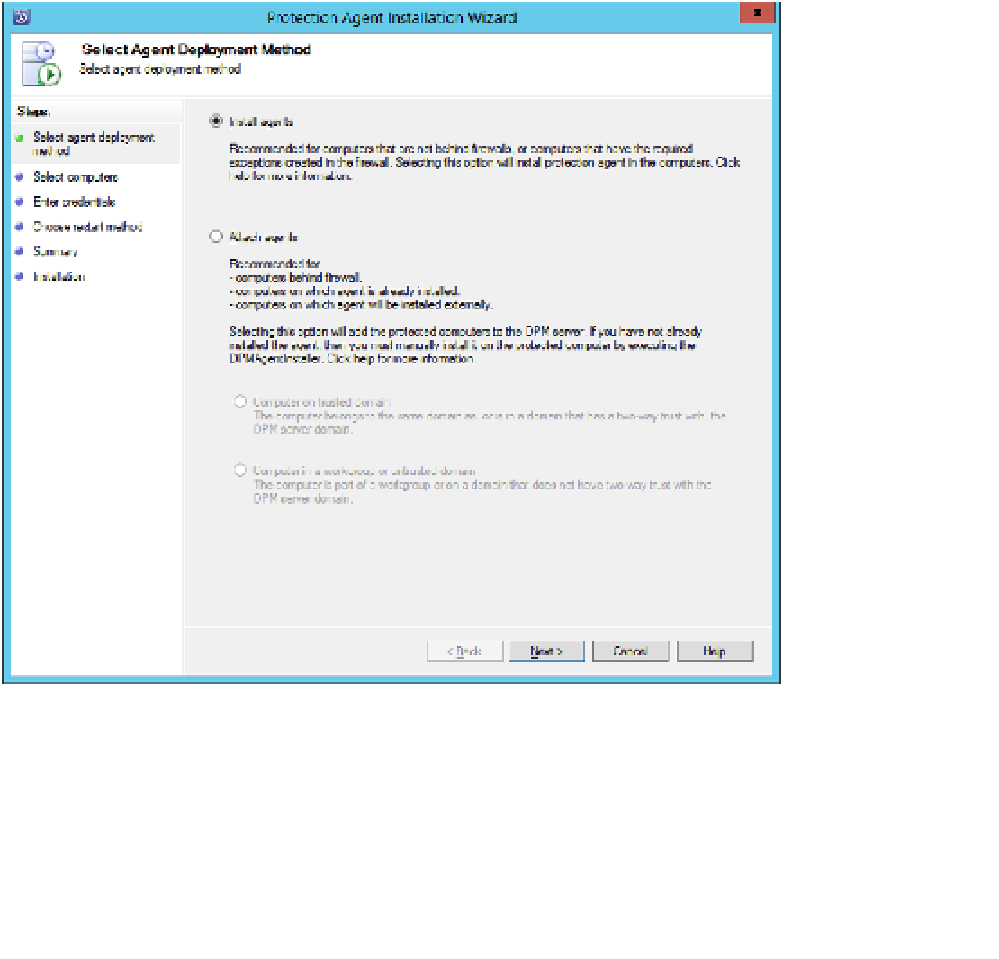
In the Management workspace of the DPM console, click Install. This will launch the
Protection Agent Installation Wizard. On the Select Agent Deployment method, shown
in Figure 5-48, choose Install Agents, or Attach Agents. You select Attach Agents for
computers that already have the agent software installed, for example those that have
the DPM agent as part of their installation image, or for computers that might be on
the perimeter network.
FIGURE 5-48
Install DPM agent