Information Technology Reference
In-Depth Information
4.2
Usage of Delegated Access Rights by CSC - Use-Case 02
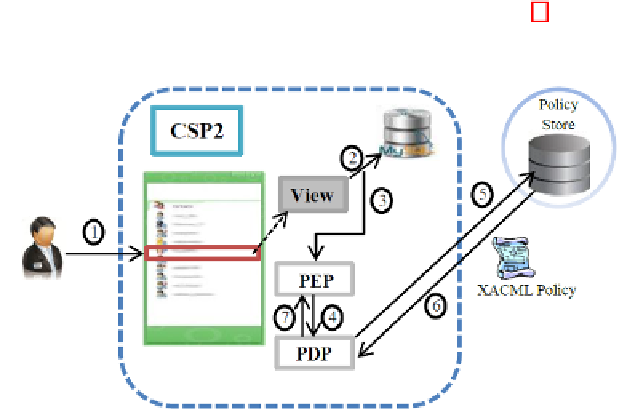
In use-case 02, we present a list of steps that the user might take to use a delegated
service. In particular this use-case depicts the complete set of steps that will be
performed after the execution of access right delegation explained in the previous
sub-section, it further assumes that the CSC is authenticated and authorized user
of Cloud. A brief overview of service usage is presented in Figure 4; however, we
elaborate each step below,
Fig. 4
Synchronization after ARD
1. Doctor B selects the record of Patient B.
2. Click on the view button result in a database query.
3. However, prior to record display, PEP captures the view record request, collects
the required attributes and prepares the query for PDP server.
4. As a next step, PEP forwards the prepared query to the PDP server for evaluation.
5. PDP server, upon receiving the evaluation requests queries its Policy store.
6. Policy store responds back with the list of most related policies.
7. PDP server evaluates the request against the provided policy set and gives
its decision (permit/deny). PEP then enforces the returned decision and either
presents the medical record of Patient B or displays an error message specifying
the details, accordingly.
5
Evaluation
Cloud Security Alliance (CSA) provides
Guidance for Identity & Access Man-
agement V2.1
[12], which offers useful practical guidelines and recommenda-
tions which may help software developers to design and analyze the functionality
aspects of their Cloud based IDMSs. According to CSA, secure IDMS for feder-
ated Cloud environment must include real-time and synchronized user provision-
ing, de-provisioning, interoperability and communication level security. In addition
Search WWH ::

Custom Search