Information Technology Reference
In-Depth Information
3
Proposed Secure IDMS for Federated Cloud Environment
In this section, we present the design and architecture of
Secure Identity Manage-
ment System for Federated Cloud Environment
. We have enhanced the conventional
IDMS by proposing and designing the secure Identity Management System for fed-
erated Cloud that addresses the security and interoperability concerns of this emerg-
ing paradigm. We have based our system on well-known industry standards such as
XACML, REST, SAML and SCIM schema. The layered architecture proposed for
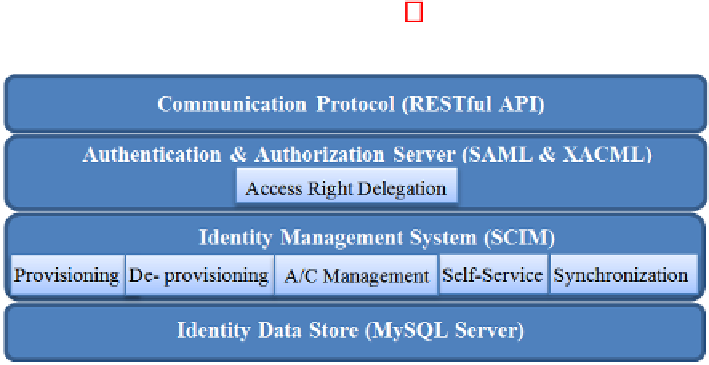
Secure Identity Management System for Federated Cloud Environment along with
the related components are presented in Figure 1. Brief description of each system
module is provided in the following subsections.
Fig. 1
Architecture of Secure IDSM for Federated Cloud Environment
1.
Provisioning:
This module is responsible for the on-boarding or creation of
user accounts using SCIM schema and REST. In the proposed system, after re-
ceiving the provisioning request from CSC, Cloud administrators collects and
verifies all the required information and stores it in its identity data store. They
further associate the CSC with some specific role according to the collected in-
formation, so that CSC's future requests for Cloud services and resources are
evaluated in the light of privileges assigned to that specific role. Cloud adminis-
trator then dispatches the CSC's information related to his verification and au-
thorization to the respective authentication and authorization servers. Listing 1
provides a non-normative example of SCIM user representation in JSON format.
2.
De-Provisioning:
or Account Deactivation module deals with the real-time and
synchronized deletion or suspension of user accounts. Upon receiving the de-
activation request, Cloud administrator issues an access revoke request to the
authorization server for immediate deactivation or suspension of CSC's access
rights from all the Cloud services and resources. However, in case of any on-
going activity or transaction, CSCs will be prompted with an error message,
stating “Your access rights have been revoked” followed by an immediate ter-
mination of their active sessions.
Search WWH ::

Custom Search