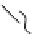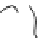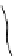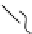Environmental Engineering Reference
In-Depth Information
A fi rst critical step here is to serve, store, and share monitoring data to use in an
adaptive management framework when combating invasive species. Initial control
eff orts may not be successful, and vulnerable habitats may be quickly re-invaded
from seeds, propagules, or source populations nearby. h us, rapid assessment
is an iterative process improved by careful monitoring and information sharing
(Stohlgren and Schnase 2006).
A second critical step is to use predictive spatial models to revise maps of cur-
rent and potential species distributions and abundance to select the next highest
priority control sites in a strategic manner. h is step may include isolating source
populations from vulnerable habitats by concentrating on corridors of invasion
or two-pronged attacks on both well-established source populations and newly
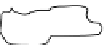
invading sub-populations (Fig. 3.2). Each habitat must be prioritized and acted
upon according to the priority it is assigned. A key feature here is documenting all
management actions to better understand the invasion process and to be able to
Future with prioritization
Contain/control site
Priority eradication
sites
Past
Present
Priority survey
sites
Early detection
and rapid
assessment areas
Future without prioritization
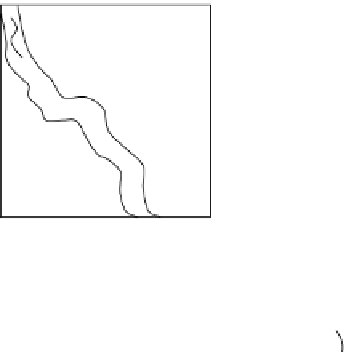
Fig. 3.2
In this conceptual model of invasion the past shows where a species
may have been introduced. The present shows where the species is when
it is fi rst found. Priority survey sites are areas between two close invasions,
contain/control sites are large patches, and priority eradication sites are areas
of small populations. If these sites are prioritized expediently the damage can
be minimized and money saved. Without prioritization, species will continue
to spread and cause more ecological and fi nancial burden. The concept of this
fi gure applies equally well to plants, animals, and diseases.