Information Technology Reference
In-Depth Information
(e.g. tokens issued by another STS), the STS will try to determine the context of
the request, the associated Circle-of-Trust, and whether this can be done based on
the security primitives available and the configuration information it holds in its
database. A fault message will be returned to the requestor if no suitable collabora-
tion context is identified or there is no matching configuration that can be fulfilled.
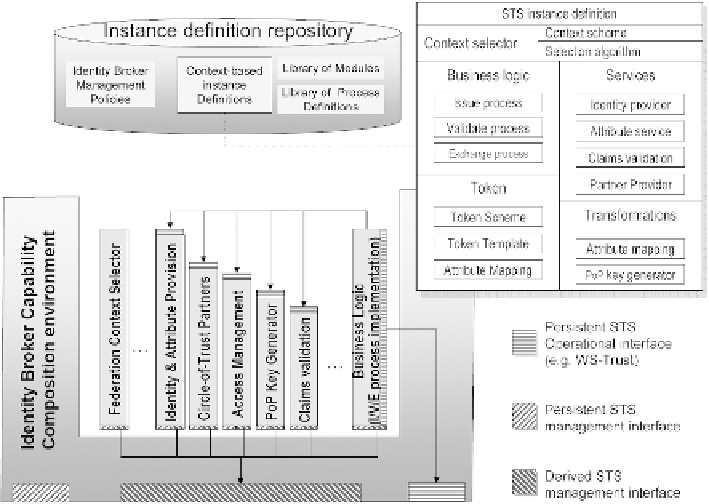
Fig. 8.3:
Overview of the Identity Broker architecture
After selecting the matching federation configuration, the Identity Broker instanti-
ates the corresponding STS business logic capability and binds it with the appli-
cable process description. It also instantiates the primitive security functions to be
composed by the business logic of the STS, such as the corresponding federation
partner provider, the claims provider and the claims validity provider and binds
them to the STS business logic process. Each of these internal capabilities of the
STS may also have a federation-context-specific configuration, which is loaded
upon their instantiation. An innovative execution mechanism by which instance
execution takes the form of separate bundles of parallel threads that are allocated
distinct memory spaces ensures high-performance during operation.
8.3.1.2 Managing Trust Relationships Among Federated Identity Brokers
Relationships between federated identity brokers form a trust network can reflect
the service-consumer relationships for a particular value network and a particular
context. Brokers can share the same federation context identifier (i.e., a shared
state reference) and associate it with their internal view of the circle-of-trust that