Java Reference
In-Depth Information
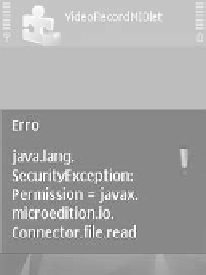
on the device (see Figure 9.2a). The user may be asked for permission (see
Figure 9.2b) and if it is denied, the
SecurityException
is thrown.
(a)
(b)
Figure 9.2
Unsigned MIDlet: a) Permission denied and b) permission request
For all but the most restrictive environments, where security domains
have been customized by manufacturers or operators, the use of unsigned
MIDlets is fine. Users grant permission when requested, perhaps once or
twice during the MIDlet's lifetime, or set them to 'Ask first time' for a
session-based grant. However, when it comes to JSR-75 (the FileConnec-
tion and PIM API), life is not so easy. Most Symbian OS devices come
with 'Ask every time' or 'Not allowed' for reading or writing user data,
and this makes it impossible for an application dependent on JSR-75 to
be of any use. Security prompts are shown too often, when reading a new
folder or listing contacts from the phonebook, and this renders all but the
most basic applications unusable.
If you want to test this scenario in practice, it is recommended that you
download the Image Viewer application that comes with [Nokia 2006c].
It is a basic file browser that can read and display folders and image files.
Running on the Nokia N95 yielded no fewer than six security prompts
from the moment it was started to the moment it was possible to see the
first image. The same happens with another JSR-75 application, [Nokia
2006d]. Every time the user presses Find Contacts to read the phonebook,
he is prompted at least four times with the same message.
The reason for such extreme prompting in JSR-75 applications is that it
deals with very sensitive data: the user's contacts and files. If all MIDlets
were to be granted access to this data, a number of nasty consequences
could happen, leading to a breach in privacy from malware spamming
the contact list or uploading private photos to some public website.
If your application is dependent on the File Connection or PIM APIs,
you will want to sign your MIDlet so it becomes usable to your audience.
As a side effect, your MIDlet also gets more permissions to use other
protected APIs. For example, unsigned MIDlets have a maximum setting