Hardware Reference
In-Depth Information
Analyzing packet dumps with Wireshark
Most sniffers have the capability to produce some kind of log file or raw packet
dump, containing all the network traffic that it picks up. Unless you're
Neo
from
The Matrix
, you're not expected to stare at the monitor and decipher the network
packets live as they scroll by. Instead, you'll want to open up your log file in a good
traffic analyzer and start filtering the information so that you can follow the network
conversation you're interested in.
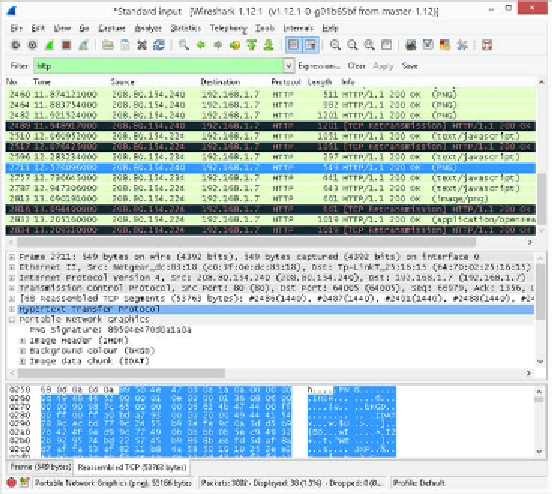
Wireshark is an excellent packet analyzer that can open up and dissect packet logs in
a standard format called
pcap
. Kismet already logs to the pcap format by default and
Ettercap can be told to do so with the
-w
argument, as in the following command:
pi@raspberrypi ~ $ sudo ettercap -q -T -i wlan0 -M arp:remote -d -w
mycapture.pcap /[Router IP]/ /[PC IP]/
The only difference running Ettercap with pcap logging is that it logs every single
packet it can see whether it matches the target specification or not, which is not
necessarily a bad thing if you want to analyze traffic that Ettercap itself cannot dissect.
There is a command line version of Wireshark called
tshark
that can be installed
with
apt-get
, but we want to explore the excellent user interface that Wireshark is
famous for and we want to keep our Pi headless.
Dissecting a HTTP conversation in Wireshark