Hardware Reference
In-Depth Information
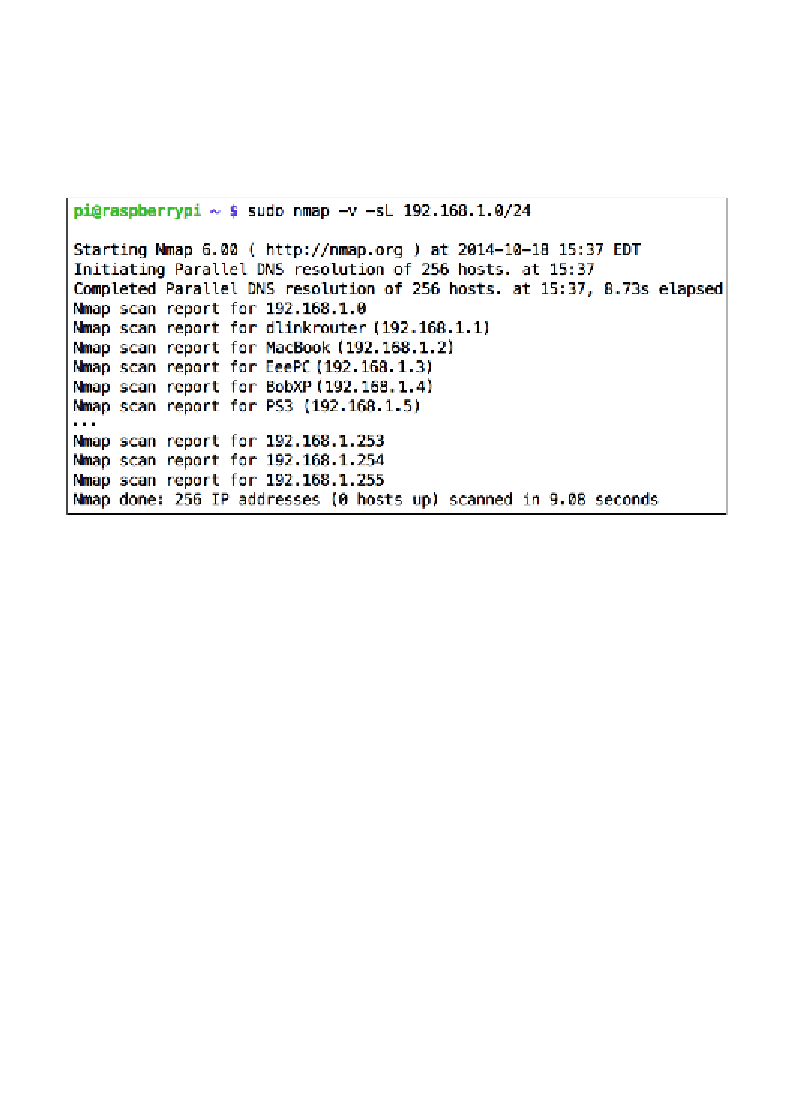
The simplest, yet surprisingly useful, scan technique offered by Nmap is called
the List Scan. It's one way of finding computers on the network by doing a host
name lookup for each IP address in the range that we specify, without sending any
actual network packets to the computers themselves. Try it out using the following
command, but replace
[target]
with a single IP address or range:
pi@raspberrypi ~ $ sudo nmap -v -sL [target]
Nmap performing the List Scan
We always want to run Nmap with
sudo
, since Nmap requires root privileges to
perform most of the scans. We also specify
-v
for some extra verbosity and
-sL
to
use the List Scan technique. At the end comes the target specification, which can be
a single IP address or a range of addresses. We can specify ranges using the short
CIDR notation such as in the preceding screenshot, or with a dash in each group
(called an octet) of the address. For example, to scan the first 20 addresses, we could
specify
192.168.1.1-20
.
The List Scan tells us which IP address is associated with what host name, but it
doesn't really tell us if the computer is up and running at this very moment. For this
purpose, we'll move on to the next technique: the ping scan. In this mode, Nmap will
send out packets to each IP in the range to try to determine whether the host is alive
or not. Try it out using the following command:
pi@raspberrypi ~ $ sudo nmap -sn [target]