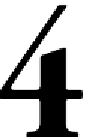Hardware Reference
In-Depth Information
Wi-Fi Pranks - Exploring
Your Network
In this age of digital information, a secret agent must be able to handle computer
networks with ease. The intricate details of protocols and network packets are still
shrouded in mystery to most people. With this chapter, you'll gain the advantage by
simply picking up and looking closely at the network signals that surround all of us
every day.
We'll start off by analyzing the Wi-Fi traffic around the house, and then we'll map
out your local network in more detail so that you can pick out an interesting target
for your network pranks. You'll not only learn how to capture, manipulate, and spy
on your target's network traffic, but also how to protect yourself and your network
from mischief.
Getting an overview of all the computers
on your network
When analyzing Wi-Fi networks in particular, we have to take the borderless nature of
radio signals into account. For example, someone could be parked in a car outside your
house, running a rogue access point and tricking the computers inside your home to
send all their traffic through this nefarious surveillance equipment. To be able to detect
such attacks, you need a way of monitoring the airspace around your house.