Database Reference
In-Depth Information
5.3 Secure Aggregation
A WSN generates huge amount of data. Computing aggregations on
these data may bring significant cost to the owner of the network. For-
tunately, there are third-party aggregators, who have the advantage of
expertise consolidation, are able to provide aggregation service on the
raw data with lower cost and better performance.
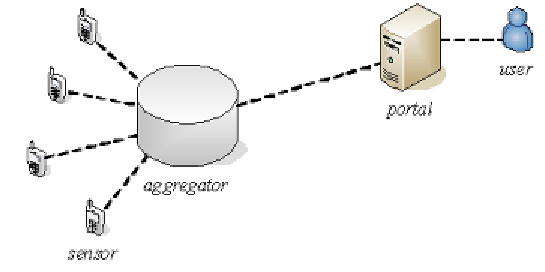
Figure 3.2
shows the
model of outsourced aggregation. The aggregator lies between sensors
and the portal, which are both facilities belonging to the data owner.
The portal, acting as a proxy, delivers data, i.e., queries and results,
between user and the aggregator. Since the aggregator is usually un-
trusted, the portal has to verify the results. The verification ensures the
results are: i) correct: the results are indeed originated from the sensors,
not faked by the aggregator. ii) complete: all data belong to the result
set are returned, none is dropped.
Figure 3.2.
Outsourced aggregation model
As a general setting, each sensor
n
i
shares a secret
k
i
with the por-
tal, which is unknown to the aggregator. The approach to ensure the
correctness is straightforward. For each raw data
d
,
n
i
computes a Mas-
sage Authentication Code (MAC for short) md using
k
i
.
n
i
then sends
the pair
<d,m
d
>
to the aggregator. The aggregator cannot generate
proper MAC for a message since it is not aware of
k
i
, while the por-
tal is able to verify the correctness using the shared keys. However,
to ensure the completeness is much more challenging. Nath et al. [41]
propose SECOA for secure aggregation on the maximum value and its
derivatives. SECOA defines a one-way rolling function
H
, computing the
digest of an input. To implement secure MAX aggregation, each sensor
n
i
computes a seed
s
i
from
k
i
. Suppose the reading of
n
i
is an integer
v
i
.
n
i
then applies
H
by
v
i
times on
s
i
(let the resulting digest be
h
i
)and