Information Technology Reference
In-Depth Information
a.
01234567890120123456789012
+x**x+xabbcae**+x+*xabbcae
b.
Sub-ET
1
Sub-ET
2
x
x
x
x
x
0.298
1.083
1.083
1.466
0.298
1.083
y
(
381
x
2
x
)
(
381
x
2
2
19258
x
)
2
762
x
2
3
19258
x
c.
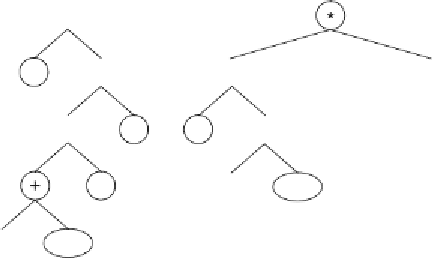
Figure 5.2.
Best solution created in the experiment summarized in the second
column of Table 5.3. This program has an R-square of 0.9999999999082 and was
found in generation 63 of run 25.
a)
The chromosome of the individual.
b)
The sub-
ETs codified by each gene (the actual values of the constants
a
,
b
, and
c
are
shown in the sub-ETs).
c)
The corresponding mathematical expression after linking
with addition (the contribution of each sub-ET is shown in brackets). Note that this
program is a very good approximation to the target function (5.1).
random numerical constants and consists of an extremely elegant, efficient,
and original way of dealing with them.
Structurally, the Dc comes after the tail, has a length equal to
t
, and is
composed of the symbols used to represent the random numerical constants.
Therefore, another region with defined boundaries and its own alphabet is
created in the gene.
For each gene the numerical constants are randomly generated at the be-
ginning of a run, but their circulation is guaranteed by the usual genetic
operators of mutation, inversion, transposition, and recombination. Further-
more, special Dc-specific operators such as mutation, inversion, and IS trans-
position, guarantee a more generalized shuffling of the numerical constants.
And there is also a special mutation operator that allows the permanent