Information Technology Reference
In-Depth Information
DEBIAN
OPENSOLARIS
WINDOWS 2000
FREEBSD
NETBSD
WINDOWS XP
HONEYD
OPENBSD
ˆ
Fig. 5.
Sketch of the time series compound of 100 samples of
R
(
t
)
5Con lu on
The paper presented the aspects related to e
ciency and reliability of tools for
remote identification of operating systems through active OS fingerprinting and
confirms the benefits of using feature extraction and pattern matching on the
analysis of TCP ISNs. The results demonstrate the feasibility of the computa-
tional intelligent methods developed by the Zion for OS fingerprinting. Since
Zion use only well-formed packets on the identification process, it can be used
against sensible machine, such as SCADA devices. We showed also the reason
for each wrong identification of analyzed tools when a set of network security
countermeasures are incorporated in test bed. We exploited the TCP ISN of
several OSes to bring about why Zion is not influenced by the use of packet
normalization or PAT and can detect SYN proxies and Honeyd.
Acknowledgment.
The authors would like to express their gratitude to the De-
partment of Exact and Applied Sciences, Department of Computer Engineering
and Automation, Federal University of Rio Grande do Norte, Brazil, and REDIC
(Instrumentation and Control Research Network) for supporting this work.
References
1. Nmap Hackers Mailing List: Top 2 OS Detection Tools (2008)
2. The
OpenBSD
Packet
Filter
(2010),
http://www.openbsd.org/faq/pf/
(OpenBSD version 4.7)
3. Arkin, O., Yarochkin, F.: XProbe2 A 'Fuzzy' Approach to Remote Active Operat-
ing System Fingerprinting. Tech. rep., Sys-security (August 2002)
4. Auffret, P.: SinFP, unification de la prise d'empreinte active et passive des
systmes d'exploitation. In: Proc. Symposium sur La Securit des Technologies de
L'Information et des Communications (2008)
5. Bellovin, S.: Defending Against Sequence Number Attacks. RFC 1948 (Informa-
tional) (May 1996)


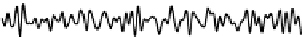
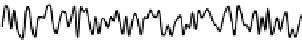
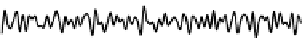

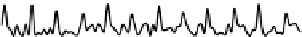

Search WWH ::

Custom Search