Information Technology Reference
In-Depth Information
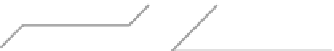
Fig. 2.
Firsttestenvironment
NetworkMiner, PacketFence and Satori) were not included in the tests. The cho-
sen tools were: Nmap [9] (version 5.21), SinFP [4] (version 2.07), Xprobe2 [3]
(version 0.3), and Zion [12] (version 0.1).
Each selected tool underwent a series of tests related to its ability to identify,
and robustness against the presence of network security devices (e.g. firewalls).
Initially, tests were conducted in a controlled environment without the presence
of security devices. In this case, the tools are, theoretically, under ideal con-
ditions. Therefore, the results related to these tests express the best possible
results for each tool. This initial test environment is shown in Fig. 2. The op-
erating systems used are installed on the machines in the right side, and in the
scanner
machine the fingerprinting tools were installed.
The OSes were chosen obeying three criteria: (i) they are widely used, so
the fingerprinting database of each tool most probably have their signatures;
(ii) just one of OSes that have the same, or almost the same, TCP/IP stack
implementation (e.g. QNX or NetBSD, MacOS or FreeBSD) [13,14]; (iii) and not
to be a newest system that probably can not be in the fingerprint databases of
some old tools like Xprobe2 (for example, there are no fingerprints of Windows 7
and Vista on Xprobe2 database). The selected OSes are shown in Table 1.
Now we introduce some security devices to create a more realistic shot of
a machine on the Internet. Assuming an environment in which the firewall is
intended to protect a given set of services (e.g. HTTP and SSH) all trac not
associated with these services could (or should) be blocked. This blockage may
imply that all UDP and ICMP trac could be discarded. As result, the tools
whose use data from these protocols will not produce reasonable results.
Regarding the trac normalization, almost all the peculiarities exploited by
TCP/IP stack fingerprinting methods, present in specially crafted packets, sent
Table 1.
Used operating systems
Operating system Detailed version
Debian
Linux debian 2.6.26-1-686
FreeBSD
6.4-RELEASE i386
NetBSD
4.0.1 GENERIC i386
OpenBSD
4.4 GENERIC#1021 i386
OpenSolaris
SunOS 5.11 snv_101b i86pc
Windows 2000
5.00.2195 Service Pack 4
Windows XP
Version 2002 Service Pack 2




















































Search WWH ::

Custom Search