Information Technology Reference
In-Depth Information
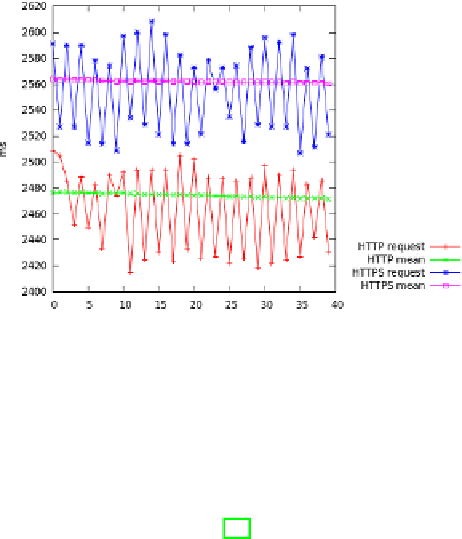
Fig. 2.
Overload introduced by the SSL secured communications, in terms of the time
response seen by the user compared to not SSL secured communications
In one case, the files were sent just like a normal Moodle distribution will do
it; in the other, they are signed by the client, sent using SSL, and verified (the
signature) by the server. The tests have been carried out in an Intel Core Duo
with 2.80 GHz, 1MB L2 cache size and 2GB RAM, acting as MS, RA and CA.
Therefore, and following the results in [11], a much better performance could be
achieved with a better designed architecture (e.g. using different machines for
the MS, RA and CA). Nevertheless, our tests show that, for this basic scenario,
the differences in terms of time responses are not too high. We show the results
obtained of one of the runs of the test in image 2. For the sake of clarity we
only depict the time response for the last 40 samples (which behave like the 80
previous samples) and the evolution of the mean values obtained from them. We
can observe that the time responses are quite similar, although the mean values
are a little bigger for SSL protected communications than for not protected
communications. The mean value of the response time obtained for unprotected
communications and SSL protected communications, is of roughly
2471
ms and
2560
ms, respectively, although in some tests the difference was slightly bigger,
but no more than a few hundreds of ms.
With respect to the changes a user will experience in the way he/she must
interact with the system, they are just minor ones. During the registration pro-
tocol, there are only two extra steps to the eyes of the user: the ticket ID and
the certificate that he will have to download. Once this is done, the added func-
tionalities affect users' day to day experience only when signing files and quizzes
(through the private keys stored in users' certificate to sign files and quizzes). In
order to do this, the user just have to tell the browser where his/her certificate is
located and introduce the corresponding password. As we have explained above,
these are just minor changes. Nevertheless, we are planning to make some tests
involving real users to obtain true feedback in this matter.
Search WWH ::

Custom Search