Information Technology Reference
In-Depth Information
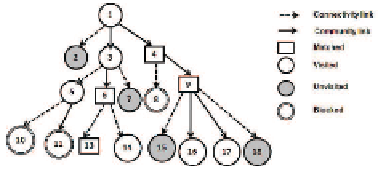
Fig. 2.
The breadth first search (BFS) tree for the search procedure initiated by peer 1
links are preferred over connectivity links to dispatch query. Peer
1 initiates a query
and forwards it to two community neighbors 3 and 4. The query reaches peer 8 via
peer 4. However, peer 8 knows that peer 4 is malicious from previous transactions.
Hence it blocks the query. The query forwarded by peer 5 is also blocked by peer 10
and 11 as both of them know that peer
5
is malicious. The query is matched at four
peers: 4, 6, 9 and 13. The search process is shown in Fig. 2.
Topology Adaptation
: Responses are sorted by the initiating peer
i
based on the
reputation of resource providers, and the peer having highest reputation is selected as
source of download. The requesting peer checks the authenticity of downloaded file.
If the file is found to be fake, peer
i
attempts to download from other sources. It up-
dates the trust rating and possibly adapts topology. The restructuring of network is
controlled by a parameter known as
degree of rewiring
which is the probability with
which a link is formed between two peers. Topology adaptation consists of the fol-
lowing operations: (i)
link deletion
: Peer
i
deletes the existing community link with
peer
j
if it finds peer
j
as malicious. (ii)
link addition
: Peer
i
probabilistically forms
community link with peer
j
if resource is found to be authentic.
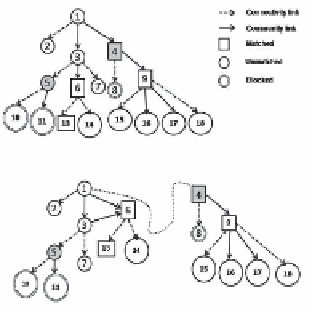
In the example shown in Fig. 3, peer 1 downloads the file from peer 4 and finds
that the file is spurious. It reduces the trust score of peer 4 and deletes the community
link 1--4. It then downloads the file from peer 6 and gets an authentic file. Peer 1 now
sends a request to peer 6, and the latter grants the request and adds the community
edge 1--6. The malicious peer 4 loses one community link and peer 6 gains one com-
munity edge. However, the network still remains connected by connectivity edges.
Fig. 3.
Topology adaptation on the search in Figure 2. Malicious nodes are shaded in gray.
Search WWH ::

Custom Search