Information Technology Reference
In-Depth Information
the specific file rather than expanding communities. For example, if peer
i
can contact
at most 10 neighbors and
Prob
com
of
j
is 0.6, it forwards query to 10 x (1 - 0.6) = 4
neighbors only. The search strategy modifies itself from initial
TTL limited BFS
to
directed DFS
with the restructuring of the network. The search is carried out in two
steps-
query initiation
and
query forward
. These are explained in the following.
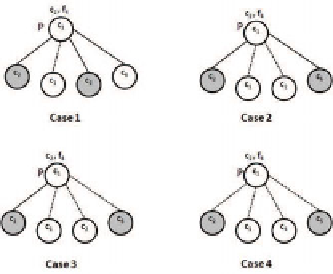
Fig. 1.
Neighbor selection at P for query string (c2, f4). Community edges and connectivity
edges are drawn with solid and dotted lines respectively. Nodes that dispatch query are shaded.
Query initiation
: The initiating peer forms a query packet containing the name of
the file (
c, r
) and forwards it to a certain fraction of neighbors along with the
Prob
com
and the TTL values. The query is disseminated as follows. The neighbors are ranked
based on both
trustworthiness
and the
similarity of interest
. Preference is given to the
trusted neighbors who share similar contents. If there are insufficient community
links, query is forwarded through connectivity links also. The various cases of
neigh-
bor selection
rule
are illustrated in Fig. 1. It is assumed that in each case only two
neighbors are selected. When the query (
c
2
,
f
4
) reaches node
P
, following cases may
occur. In first case,
P
has adequate community neighbors sharing file in category
c
2
,
hence they are chosen. In
Case 2
, there are insufficient community neighbors sharing
file in the requested category, the community neighbors sharing
c
2
and
c
6
preferred to
the connectivity neighbor
c
2
to forward query. In
Case 3
, only one community neigh-
bor (
c
2
) shares the file. Hence it is chosen. From the remaining connectivity
neighbors, most trusted
c
6
is selected. In
Case 4
, only connectivity neighbor are pre-
sent. Assuming all of them at the same trust level, the matching neighbor
c
2
is chosen
and from the rest
c
5
is selected randomly. When a query reaches from peer
j
to
i
, the
latter performs the
query forward
action, which is described in the following.
Query forward
: (i)
Check trust level of peer
j
: Peer
i
checks trust rating of peer
j
through
check trust rating
algorithm (explained later). Accordingly, the decision re-
garding further propagation of the query is taken. (ii)
Check the availability of file
: If
the requested file is found, response is sent to peer
j
. If TTL value has not expired, the
following steps are executed. (iii)
Calculate the number of messages to be sent
: It is
calculated based on the value of
Prob
com
.(iv)
Choose neighbors
: Neighbors are chosen
in using
neighbor selection rule
. The search process is shown in Fig. 2. It is assumed
that the query is forwarded at each hop to two neighbors. The matching community
Search WWH ::

Custom Search