Information Technology Reference
In-Depth Information
i
,
L
i
m
i
1
Request
,
(1)
R
c
Generate
Random
if
*
i
i
*
(
i
i
!
0
)
and
(
h
(
L
)
L
)
i
*
i
extid
i
g
(
id
,
i
)
i
m
*
L
m
*
L
i
i
else
end
Generate Random
extid
c
R
,
extid
(2)
if
extid
g
(
id
,
i
)
c
rep
h
(
id
,
R
)
else
Generate
end
Random
rep
rep
(3)
if
id
prev
m
id
rep
h
(
id
,
R
c
)
id
prev
m
id
id
m
f
(
id
)
id
m
f
(
id
)
Reader
Tag
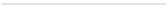
Fig. 3.
The forward rolling trigger protocol proposed by Lim
et al.
[2]
challenges and related responses from the tag. The attacker can use this
dictionary later to impersonate itself as the real tag to the legitimate reader.
2. As another attack, the above mentioned dictionary can be used to track a
specific tag. The attacker would repeatedly send the request message and
R
to all tags and look for the
g
(
id, R
) response known from the dictionary.
3. After the legitimate reader sends a request message to the tag in step (1) and
before step (3), an attacker can repeat step (1) and send a request message
to force the tag to reset the random challenge
R
. Since the new random
challenge is different from the previous one, the
h
(
id
R
) message which the
◦
reader sends will not be accepted by the tag.
After the challenge-response trigger protocol, another scheme named the
“forward rolling trigger” was proposed in [2]. This scheme takes advantage of
Lamport's one-time password authentication scheme [9]. In the “forward rolling
trigger” protocol, the tag only responds to a valid challenge from the reader or
sends back some random values otherwise [2]. In this protocol, the reader stores
a chain of hash functions like
h
(
w
),
h
2
(
w
)=
h
(
h
(
w
)),
..., h
max
(
w
), where
h
is a secure one-way hash function,
w
is a secret random seed, and
max
is the
length of the chain. The reader uses a hash value from this chain to authenticate
itself to the tag over time. For each tag in the system, the last successful session
(communication with the reader) is stored as
i
∗
and the current session is shown
by
i
. The reader uses
L
i
=
h
max−i
(
w
) to authenticate itself to the tag. The
communication process is shown in Fig. 3. As in the challenge-response trigger
protocol, an entry is not deleted from the database after the third step, but a
copy of the previous
id
is kept until the next successful session. The forward
rolling trigger protocol has some security drawbacks, as stated below:









Search WWH ::

Custom Search