Information Technology Reference
In-Depth Information
Request
(1)
i
m
i
1
*
'
i
i
i
h
(
id
),
h
(
i
$
id
),
'
i
(2)
*
i
'
i
i
Generate
Random
r
r
,
h
(
r
$
i
$
id
)
(3)
if correct:
id
m
f
(
r
,
id
)
id
m
f
(
r
,
id
)
i
m
*
i
i
m
*
i
Reader
Tag
Fig. 1.
The RFID protocol proposed by Henrici and Muller [1]
use complex cryptographic protocols in future RFID tags. Most RFID researchers,
however, believe that the industry needs simple and low cost RFID tags (below 5
cents per item) with limited number of logical gates [5],[8]. For this case, many ap-
proaches that are based on the lightweight cryptographic solutions and protocols
have been suggested [1-4]. Lightweight protocols have the advantage of keeping
the computational demand and the price of RFID tags very low. In this work,
we perform a security analysis of five lightweight protocols proposed in [1-4], and
show that they are vulnerable to some simple security attacks.
2Hen -Muller RFID Protocol
In this Section, we explain the protocol proposed by Henrici and Muller [1].
In this protocol, each tag contains its current identifier
id
, the current session
number
i
, and the last successful session number
i
∗
. Similarly, the database
contains a list of all identifiers, session numbers and the last successful session
numbers for all the tags in the system. Both the reader and the tags are aware of
the hash function
h
,and
is a “simple XOR function” [1]. The communication
process is performed as shown in Fig. 1. It should be noted that in this protocol,
an entry is not deleted from the database after the third step, but a copy of the
previous
id
and
i
∗
is kept until the next successful session.
Although this protocol is simple, ecient and can solve many security issues
of RFID systems, it is vulnerable to some simple attacks as explained below:
1. In this protocol, the tag increases the value of
i
by one, even if the session
finally fails, while
i
∗
is updated only if the session is successful and the
reader is confirmed. Based on the above, an attacker can interrogate a tag
several times to abnormally increase
i
and
Δi
. Therefore, an attacker is
able to recognize its target by identifying and “tracking” the tag that sends
abnormally large values of
Δi
.
2. After step (2) and before the legitimate reader sends
r
and
h
(
r
◦
id
)to
the tag, the attacker can use a null element like
r
= 0 and sends back the
◦
i
◦
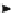







Search WWH ::

Custom Search