Database Reference
In-Depth Information
Figure 12-4.
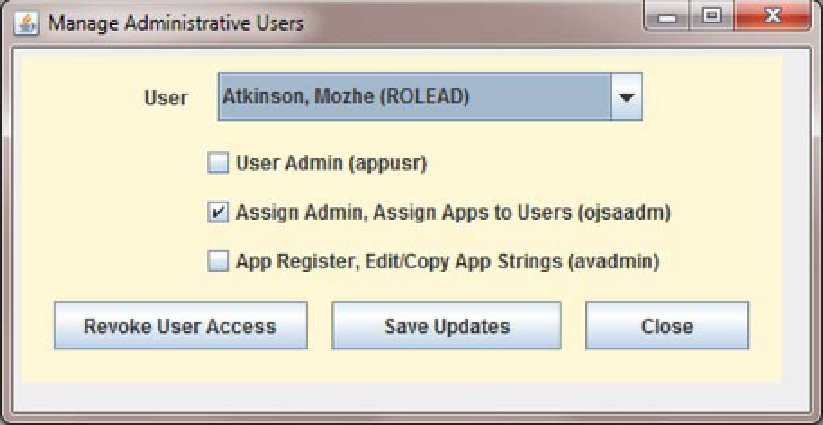
Admin Users functional screen
Also on the Admin Users screen, you will see three check boxes: one for each administrative proxy
user:
appusr
,
ojsaadm
, and
avadmin
. When a user is selected from the drop-down list, these checkboxes
will be populated with checkmarks or blanks corresponding to the current proxy grants for the user. By
selecting or deselecting these check boxes and clicking on the Save Updates button, the application user
can grant and revoke those privileges from the selected user.
There is one more button on the Admin Users screen, the Revoke User Access button. The function
of this button stops short of deleting the Oracle user account; however, it revokes all the application
grants that the user has, including the grant to proxy through
appver
—so the user in effect can no longer
use our applications.
Create the OJSAAdm User
In the Admin Users functional screen, we are connecting to the
orcl
instance as the
ojsaadm
user. This is
one of the proxy users we listed in Table 12-1. We need to create that Oracle user, and we need to grant
him access to the
HR
views needed to populate the
userComboBox
. We will do this on the
orcl
instance as
the Security Administrator,
secadm
user. The commands we are going to use are shown in Listing 12-26.
When you execute those commands, substitute the OS username of the person you want to have
manage the lists of administrators for the placeholder
osadmin
, and give the new
ojsaadm
user a strong
password.
Listing 12-26.
Create the OJSAAdm User
GRANT create_session_role TO ojsaadm IDENTIFIED BY password;
CREATE ROLE ojs_adm_admin IDENTIFIED USING appsec.p_check_role_access;
ALTER USER osadmin GRANT CONNECT THROUGH ojsaadm;
GRANT SELECT ON hr.v_employees_public TO ojs_adm_admin;
GRANT SELECT ON hr.v_emp_mobile_nos TO ojs_adm_admin;
GRANT CREATE DATABASE LINK TO ojsaadm;