Database Reference
In-Depth Information
After establishing the OS identity, we explored the code needed to use that identity when
authenticating to Oracle Database. The end goal is that our Oracle application users will be able to use
our applications without entering their passwords. In fact, they won't need passwords at all on Oracle
database, but we will be able to track each user's actions by one of two methods:
1.
We set the connection client identifier equal to the user ID and then assure it
exists in the connection before granting access. We can then find that client ID
in the audit trail logs.
2.
We create an Oracle user for each Windows/UNIX user, although the Oracle
user does not need a password or any privileges besides
CONNECT
. We then
proxy those individual users through our application user. We can query the
audit logs for the proxy user identity.
We explored several varieties of Oracle connection pools we might establish. There are three
connection pool technologies we may use:
1.
Lightweight, thin client connection pools
2.
Heavyweight, OCI connection pools
3.
Universal connection pooling (UCP)
Finally, we built some
setConnection()
methods in
OracleJavaSecure
that make it easy for an Oracle
application developer to tap into this technology.
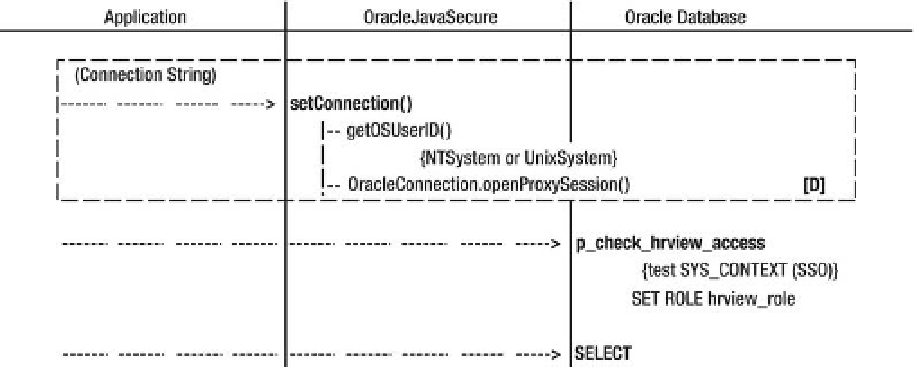
Figure 8-1 illustrates the basic SSO process. The client application calls
OracleJavaSecure.setConnection()
method with an appropriate connection string. That method further
calls
getOSUserID()
which gets the user ID (username) from the operating system using
NTSystem
or
UnixSystem
, as appropriate. With that OS user ID, we open a proxy session for our
Connection
through an
Oracle user by the same name.
Using our proxy session, we call the
p_check_hrview_access
procedure, which assures our SSO
credentials are in order, then sets the secure application role,
hrview_role
. At that point, we have done
SSO to Oracle database—notice we didn't enter a password for the specific Oracle user. We can then
select sensitive data from the
EMPLOYEES
table using the privileges granted to
hrview_role
.
Figure 8-1.
SSO procedure