Information Technology Reference
In-Depth Information
Oracle
Fusion
Applications'
security
concepts
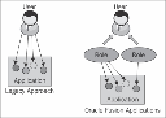
Oracle Fusion Applications handles security by addressing functional security as op-
posed to user security. Legacy applications focused on business users created an ac-
cess profile for each user. This worked well when each user had a clearly defined set
of tasks and there was a minimal overlap in the functionality between users.
Business and technology have evolved, such that application users have multiple
roles. These roles and functions are overlapping and change over time. Hence,
Oracle Fusion Applications have taken an approach that is role-based as opposed to
user-based.
This approach to security uses the function and the data that it works on as the fun-
damental units of security. These functions can then be grouped together in vari-
ous combinations to create higher-level groupings. However, this grouping does not
change the atomic level at which Oracle Fusion Applications are secured.
This approach that secures both the business activity and its corresponding data sub-
set is unique to Oracle Fusion Applications. Although the approach is not unique (it
is referred to as Role-Based Access Control), the granularity at which it is enforced is
fundamentally different.
Besides internal security aspects, the application perimeter needs to be secured as
well. Oracle Fusion Applications' security is built on the
Oracle Identity Management

Search WWH ::

Custom Search