Database Reference
In-Depth Information
For security buffs out there the key point is this: The configuration file that contains the mapping of individual
users to the privileges they can run is protected from that
delegated
root privilege. This means that delegated root
cannot administrate the PowerBroker controls itself.
/etc/pb/cloudcontrol.conf
should not be writeable by
delegated root privilege.
The fact that this mature privileged access control is built into EM goes a long way to solving many of the PAC
issues that have existed in Oracle since the beginning.
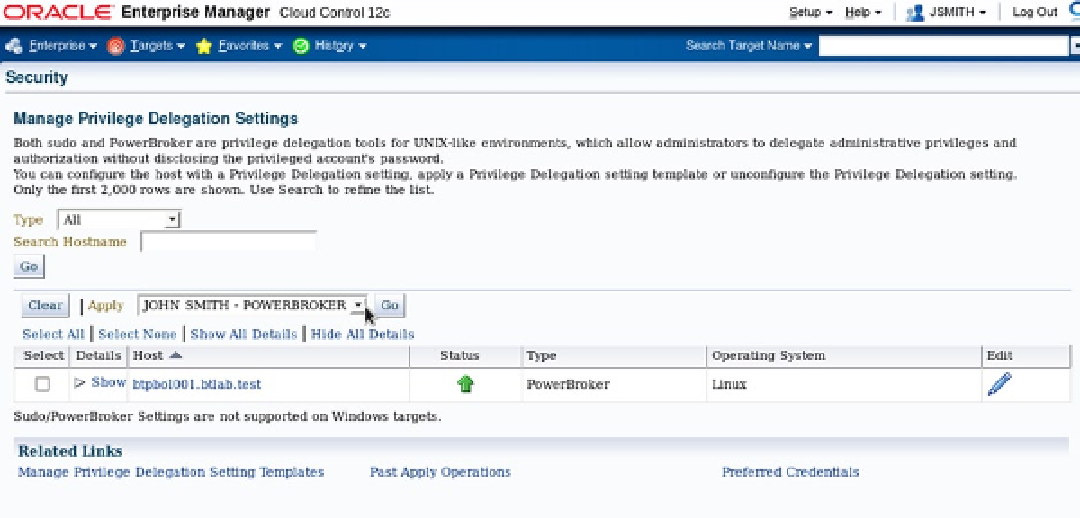
Figure
19-5
shows what the integration looks like.
Figure 19-5.
Using PowerBroker from within Enterprise Manager 12c
Additionally, BeyondTrust has a password vault product that can be used to automatically cycle the passwords
that are stored in Enterprise Manager. EM12c on its own requires the DBA or SA to input their root/DBA passwords
into the EM system for use as a named or preferred credential in the future. The problem with this is that the value
needs to be changed over time to protect against brute-forcing of the value, or from the value becoming shared.
Carrying out that password maintenance manually would be an inefficient task. So BeyondTrust's integration with
their password vault can take over that credential management.
There is a massive caveat to the PowerBroker usage, however. In the above screenshot it will be obvious that a
user acting as plain root could edit the
cloudcontrol.conf
. So the system's security depends on not giving direct
root out to the DBAs. So installing YAST and running root commands as root undermines the point of having a
PowerBroker install. With PowerBroker there should not be any reason to ever have to give the root password or
control over that password to an Oracle DBA as long as you can list the root commands that they need. Those “root”
commands can be delegated individually within the
cloudcontrol.conf
file. Thus, PowerBroker can handle some of
the cloud-based privileged account requirements.
“With PowerBroker Identity Services, companies can securely extend an existing, on-premise Active
Directory deployment to the cloud to authenticate users to cloud-based Linux servers, monitor
and report on sign-on activity, and define and implement group policies to control your cloud
server configurations.”
http://www.beyondtrust.com/content/whitepapers/wp043_Cloud_