Database Reference
In-Depth Information
Applying a Corrective Action
This concept can be used with other security parameters that we don't want on all the time due to their performance
hit; for example, auditing. Why not audit more frequently if monitoring metrics suggest that there is reason to believe
that risk is high?
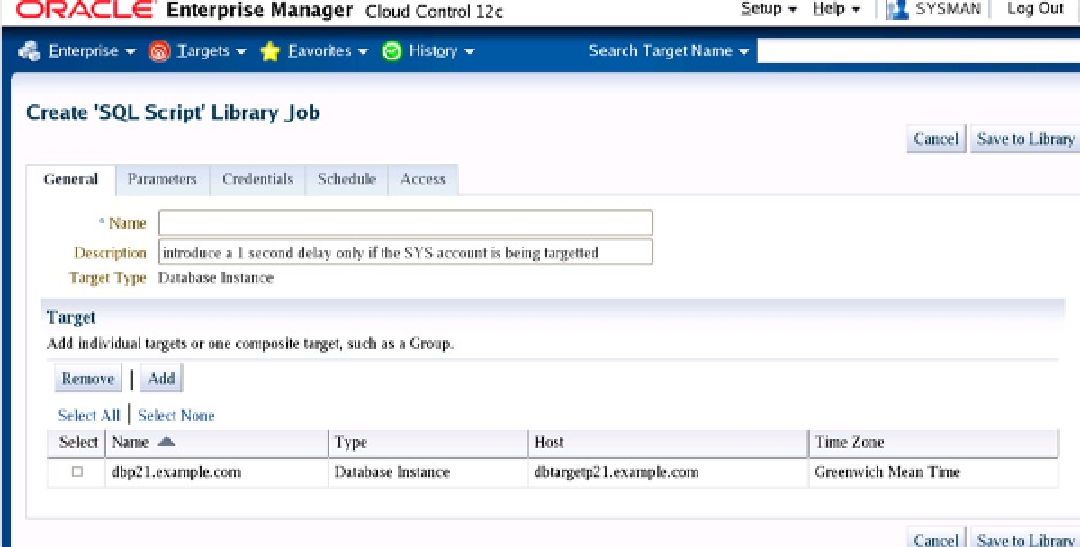
Figure
18-26
is a research lab example and would need testing for your production systems. The problem with
this setup is that the default collection period for a database is thirty minutes. Thus there will be at least a thirty-minute
reaction to the start of an attack from machine to machine. This is why a peer-to-peer syslog native IPS is quicker.
Figure 18-26.
Apply corrective action to the target
Of course, the ultimate defense against a brute-force attack of SYS is to set a very complex and unpredictable
password using characters such as those shown below:
SQL> alter user sys identified by "%^@$*()_+~`-=[{}\|;:,<.>";
User altered
SQL> select value from v$parameter where name='remote_login_passwordfile';
VALUE
-----------------------------------------------------------
EXCLUSIVE
Or you could turn off remote passwords for SYS, with restart needed, but that will lock out remote SYS sessions so
it's probably not suitable for most organizations.
SQL> alter system set remote_login_passwordfile = NONE scope = spfile
SQL> select value from v$parameter where name='remote_login_passwordfile';
VALUE
-----------------------------------------------------------
NONE