Database Reference
In-Depth Information
All the public reports are put into that standard directory, which more often than not will contain some sensitive
data due to the ease with which public reports can be made and used.
Wallet Security
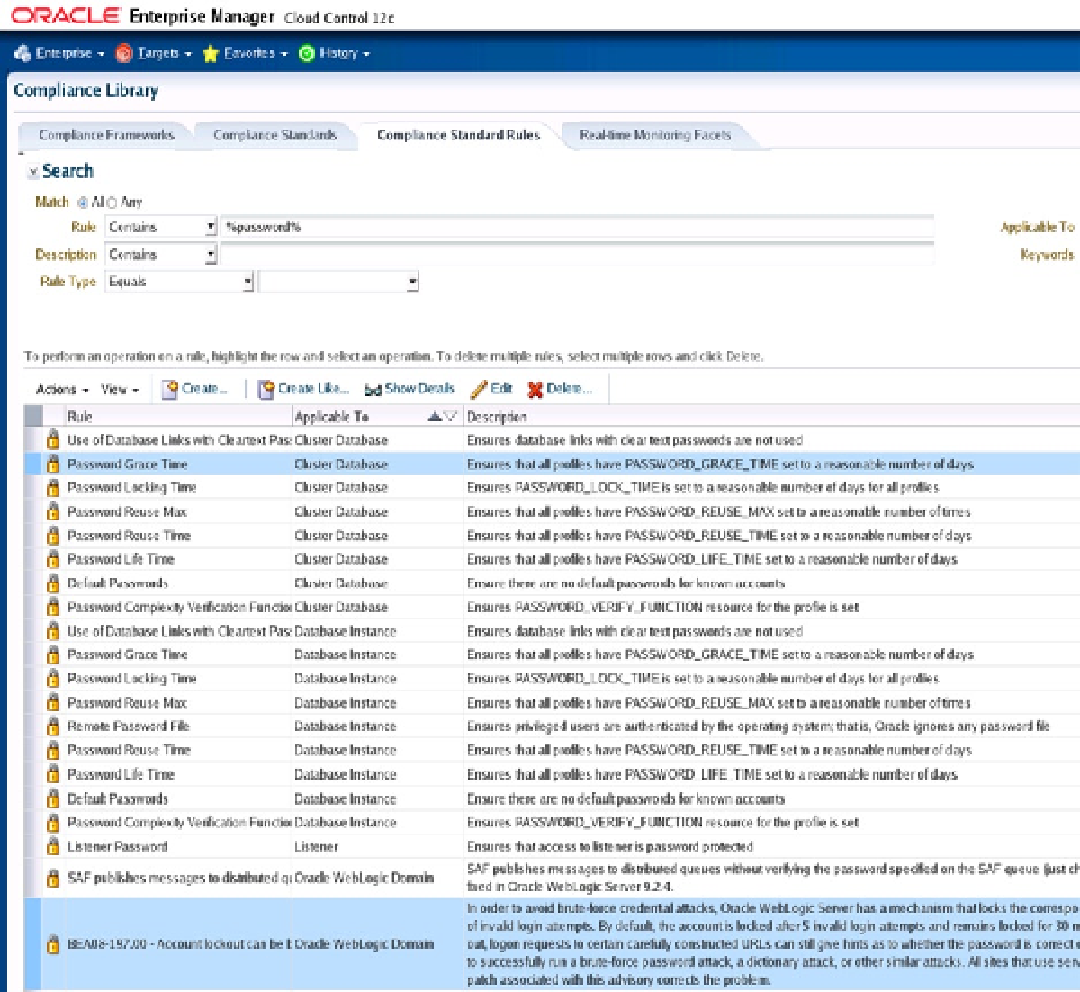
One observation I have about the in-built EM security checks is that there are a lot of checks on passwords but none
checking permissions on wallets, as can be seen in Figures
18-17
and
18-18
.
Figure 18-17.
Look at all the password policy rules