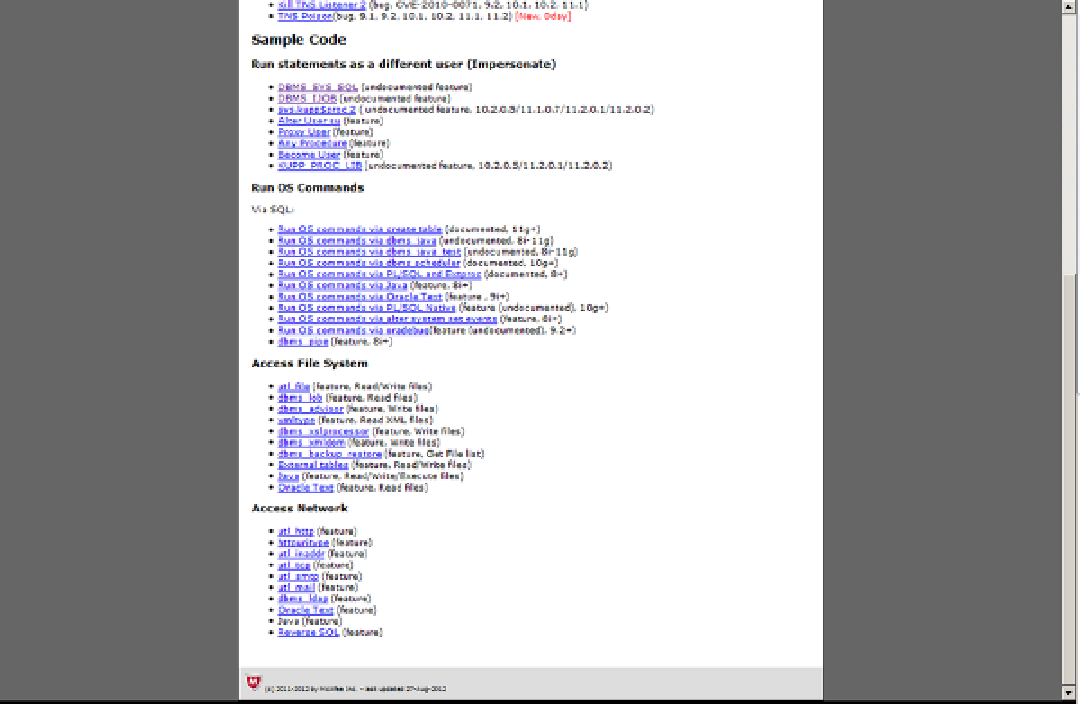
Database Reference
In-Depth Information
Figure 18-16.
Security scanner list of exploits affecting the 12c OMR (Part 2)
It is surprising that the OMR does not use a more recent version of the DB. Many of the issues just mentioned are
internal privilege escalations. The remote DoSes listed are proofed on Windows, not *nix so not so relevant to practise,
but 11.1 does have significant issues which require some expert defense.
Defending the Repository
Installing PSU is a defense against these issues. A non-patchable way to attack a repository DB is with a TNSPOISON
attack. By registering a rogue instance to the listener an attacker can proxy commands and insert their own SQL
(create user hacker, grant DBA to hacker). COST SSL from instance to listener for EM OMR should be considered as
a high priority for OMR, as is securing this whole EM install, as that security is the foundation to the whole estate's
security. TNSPOISON attack and COST protection was discussed in Chapter 10.
At the time of writing EM is not able to monitor listeners that are TCPS only, so the above compatibility would
need to be checked with MOS SR. See this Support Note: