Information Technology Reference
In-Depth Information
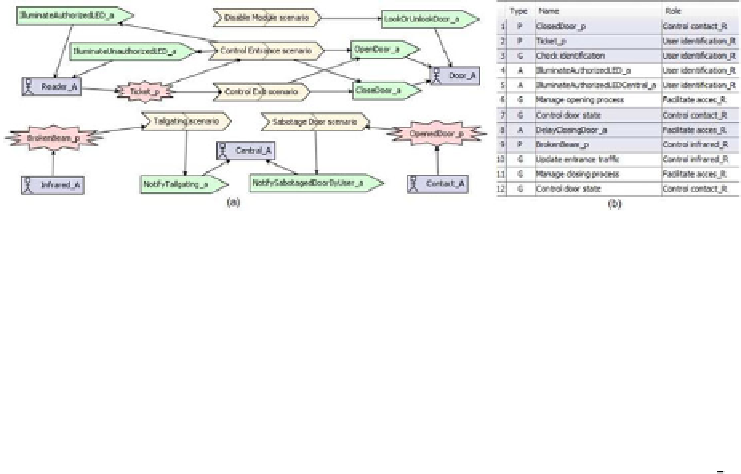
Fig. 1.
(a) Analysis overview diagram; (b) Steps of Control Entrance scenario
3.1 System Specification Phase
Usually, the system specification phase begins with the
analysis overview dia-
gram
, which shows the interactions between the system and the environment
(see Fig. 1a). At this level, firstly, an
actor
for each device of a module (reader,
door, infrared and contact sensors) has been identified; there is also a
Central A
actor representing the user interface that supports the human interaction with
the system, that is, it shows the monitored activities to the security guard, and
the commands he/she can send to the system to disable modules. Moreover, on
the one hand, the information that comes from the environment is identified as
percepts
. For example, the code associated to the card introduced by the user
into the reader (
Ticket p
) and the signal captured by the infrared device when its
beam is broken (
BrokenBeam p
). On the other hand, every operation performed
by the system on the actors is identified as an
action
. For example, the com-
mands issued to open and close a door (
OpenDoor a
and
CloseDoor a
)andalert
messages displayed on the user interface to notify that an anomalous situation
happens (
NotifySabotagedDoorByUser a
and
NotifyTailgating a
). Finally, rela-
tions with the scenarios identified to control the entrance, the exit and anomalous
situations are established (see
Tailgating
and
Sabotage Door
scenarios).
A scenario is a sequence of structured steps - labeled as action (A), percept
(P), goal (G), or other scenario (S) - that represents a possible execution way
of the system. As an example, Fig. 1b illustrates the process performed by the
system to control the crossing of authorized users through a module. This sce-
nario begins when it is perceived that the door is closed (step 1) and the user
introduces his/her identification ticket into the reader (step 2). Then, the user
database is queried to check if this ticket belongs to an authorized user (step 3).
Based on this information, the LEDs are illuminated to notify which result is
obtained with this checking (steps 4 and 5). After, the door is opened (step 6),
the door state is supervised (step 7), a delay is introduced allowing the user to
cross the module before the door is closed again (step 8), it is perceived when
the infrared sensor is interrupted (step 9), the counter of people that cross the
module is updated (step 10) and the process to close is started (step 11). The
scenario finishes monitoring the door state (step 12).







Search WWH ::

Custom Search