Information Technology Reference
In-Depth Information
is encrypted, an attacker may access data in memory using a worm or virus. So we
must assume that an attacker can access to the database, and retrieve any data stored in.
Fig. 10.
Attacks via Record Multiplicity
In Figure 10, we show multiple enrollments for same biometric template T. Each
enrollment has its secret S, and secret S is encoded (F
1
(S
1
) to F
n
(S
n
)). It is transmitted
and stored by different systems. An attack via record multiplicity(ARM) is that if an
attacker can obtain several of these encodings, he can correlate the data contained
encodings to link the databases, and may obtain some cases to directly retrieve T and
S
1
. . . S
n
.
In fuzzy vault scheme, an encoding is called a vault. The vault is constructed by
user's minutiae and chaff points. We assumed that two or more fuzzy vaults that are
generated using the same fingerprint which are stored in different system. Since the
minutiae points in vault generated from same fingerprint, if an attacker obtains two or
more fuzzy vaults, he can obtain minutiae in vault as compare with each vault.
Fig. 11.
Surreptitious Key-Inversion Attack(SKI)
5. Surreptitious Key-Inversion Attack[9]
This attack assumes that an attacker can obtain a secret of authorized user by a weak
point between different modules of the system. For example, if secret S is an ID for
user login or a cryptographic secret key, it may be possible to intercept secret S as
submitted or used in authentication or verification system, by an insider. In case of an
external attacker, traditional system is easily attacked by unprotected data transmis-
sion, unencrypted memory or has utilized Trojan horse programs to intercept data.
Figure 11 shows surreptitious key-inversion attack(SKI).
In fuzzy vault scheme, secret S is added CRC(Cyclic Redundancy Check) code,
then is used as coefficient of polynomial. An attacker can obtain minutiae points of
authorized user by comparing with the vault and the polynomial. In this case, the
vault is that minutiae point adds chaff point, and the polynomial is constructed with
given coefficients.

































































































































































































































































































































































































































































































































































































































































































































































































































































































































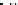

































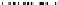













































































































































































































































































































































Search WWH ::

Custom Search