Database Reference
In-Depth Information
Coniguration
The
contrib/swekey.sample.cont
sample file should be used as a starting point
to configure this feature. This file contains sample configuration commands and
comments from the vendor. The principle is simple—each Swekey device contains
a unique id, and this id must be associated with a MySQL username in the Swekey
configuration file. These lines are part of the sample file:
0000000000000000000000000000763A:root
000000000000000000000000000089E4:steve
0000000000000000000000000000231E:scott
This means that the person responsible with the phpMyAdmin configuration, tracks
which Swekey is given to each user and puts this information in the file. The vendor
does not need to be informed about this association. They only keep track of which
Swekey are sold and which are deactivated. Hence, Swekey can be passed from one
user to another, provided that the configuration is updated accordingly.
Other security-related directives are in the sample file, and it's recommended
to refrain from changing them—
SERVER_CHECK
,
SERVER_RNDTOKEN
, and
SERVER_STATUS
in particular. This is because these directives access servers via https,
which is a guaranty of a secure channel between our web server and the vendor's.
Once modified, this file should be copied over to a directory outside the web server's
document root (suggested place is
/etc/swekey-pma.conf
). Then, a configuration
parameter in
config.inc.php
must be set as well:
$cfg['Servers'][$i]['auth_swekey_config'] = '/etc/swekey-pma.conf';
Usage
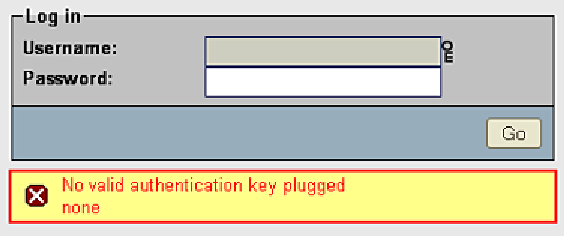
Let's see what happens now when phpMyAdmin is started and no Swekey is
connected to your workstation:


Search WWH ::

Custom Search