Information Technology Reference
In-Depth Information
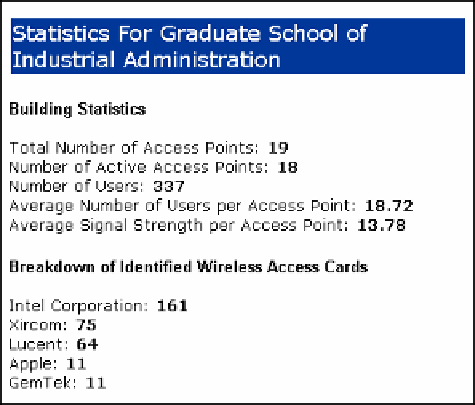
Fig. 4.
Building Specific Information.
access and eavesdropping of data. Using range-extending antennas and packet
sning software a malicious user can capture data flowing across a network
from a considerable, on the order of miles, distance away from the network.
From an administrative point of view a wireless LAN map, in combination with
statistical data, greatly aids network administrators in locating access points
with high bandwidth requirements, pinpointing unused nodes, locating rogue
access points and discerning network usage and trends over time.
5 User Movement and Mobility
Context-aware application developers should have a thorough understanding of
their user communities. One common assumption is that the terms 'mobile' and
'wireless' are synonymous. Utilizing the data from wireless network mapping and
location services this assumption has been put to the test by determining the
mobility of users and basic information about their movement patterns.
A data set encompassing over 10,000 wireless devices was studied at Carnegie
Mellon University on its Wireless Andrew network [9]. Using unique MAC ad-
dresses, wireless devices were tracked over the course of a four month period. This
data allowed for a thorough study of mobility and movement patterns. Similar
studies have been done at Dartmouth [12] and Stanford University [20, 21].
5.1
Two Distinct Communities
A quick analysis of the data set shows that there are two distinct user commu-
nities on campus. The first community is the Carnegie Mellon Tepper School of
Business (GSIA) which represents slightly more than one thousand users. This
Search WWH ::

Custom Search