Information Technology Reference
In-Depth Information
1.4.2.1
Security Structure for the CROWN Node
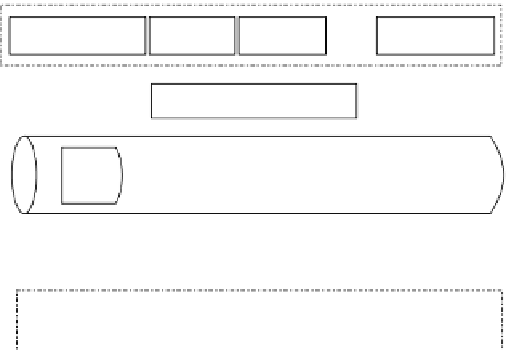
Figure 1.10 depicts the internal security structure for the CROWN node.
The design of this structure is much inspired by Axis, although the purpose
of CROWN Security is message-level security processing rather than SOAP
message processing. The security processing depends on coni gurable
security chains, and generally two chains, which deal with the request and
response messages of service respectively, are coni gured for every grid
service. For the sake of simplicity, there is only one processing chain shown
in Figure 1.10. Each handler in the processing chain is in charge of some
specii c security functions. The grid services developers, deployers, and
administrators can customize grid services protection by merely coni gur-
ing these chains. The coni guration is stored in security descriptors.
When the message interceptor embedded in the CROWN node inter-
cepts a request or response message for a grid service, it will call the
engine with information related to this message. The engine will then
generate an appropriate chain by means of a coni guration engine accord-
ing to the security descriptor, and invoke the chain to process the
message; that is, it will invoke each handler in the chain in a sequential
order. After invoking a handler, the engine will choose to continue the
process or terminate it according to the current result. The coni guration
engine can also be used to cache the instantiated processing chains and
handlers in order to achieve better performance.
Conversation
context
Policy
context
ATN
context
Resource
context
Context manager
Security
config
Config engine
Encry/decry
handler
Auth
handler
ATN
handler
AC
handler
Interceptor
FIGURE 1.10
Security architecture of the CROWN node.






















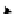
















Search WWH ::

Custom Search