Information Technology Reference
In-Depth Information
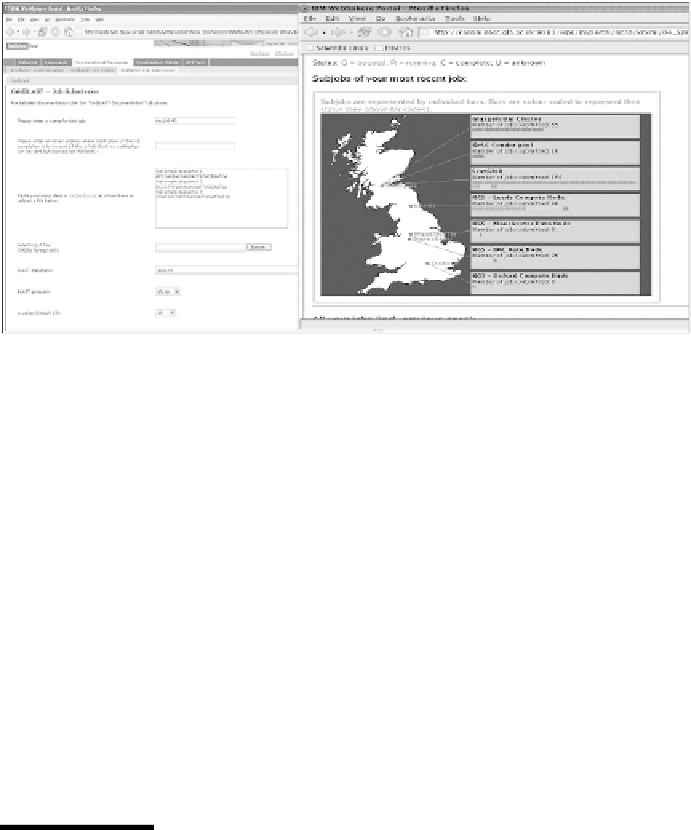
FIGURE 12.3
BRIDGES Grid BLAST front end and running/monitoring jobs.
The actual selection of where to submit a user job was based on the avail-
ability of resources (which was established dynamically). In accessing and
using the BRIDGES portal, users could simply redirect their browser from
the GEMEPS or VOTES portal to the BRIDGES portal and automatically
access and use services without the need for further reauthentication. The
front end to the Grid BLAST service is accessible as shown on the left of
Figure 12.3. This provided access to a range of genomic and microbial data
resources predeployed on major HPC resources. To support large-scale
BLAST usage, users were able to select options that allowed them to be
emailed the results when the jobs completed, or they could interactively
see the status of the jobs across the various grid resources (whether they
are queued, completed, or running), as shown in the right of Figure 12.3.
12.6
In this chapter we have explored the current limitations of authentication-
only-based solutions with PKIs as the basis for grid security. Lack of gran-
ularity of authorization will dissuade large groups of researchers from
engaging. Perhaps more of an issue are the initial steps through which
researchers are asked to proceed before they are able to do anything “on
the grid.” X.509 certii cates and the process of acquiring one and convert-
ing it to appropriate formats is a hurdle that a large swathe of the non-grid
research community will not overcome. It needs to be made simpler and
ideally removed completely. Shibboleth offers one possibility through
which the usability factor for end users can be addressed.
Conclusions and Recommendations
Search WWH ::

Custom Search