Information Technology Reference
In-Depth Information
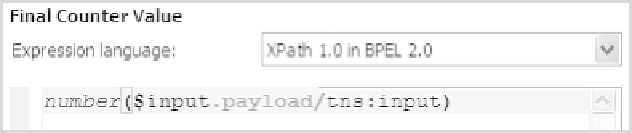
FIGURE 8.4
An example of XPath expression.
Last but not least, users of BPEL Designer always benei t from existing
features of Eclipse IDE out of the box. Eclipse is one of the most inl uential
development platforms in recent years. The open architecture fosters fruit-
ful plugin developments to integrate extension functionalities to the classic
platform. It is a handy toolbox where software components can be easily
assembled and customized in the way that best facilitates user develop-
ments. Putting any third-party software aside, there are already a good set
of features worth mentioning: error reports, CVS control, Ant scripting,
server integration, help system, online update, and many more.
8.12
A trustworthy modeling environment should guarantee the correctness
of BPEL documents being generated as a result of user interactions. While
usability features may vary from tool to tool, validation in BPEL is strictly
required by the specii cation. Besides the XSD schema that can be used for
syntactic validation just like any XML language, static analysis must be
performed additionally to detect semantic violations in the process dei ni-
tion. Since users are mediated by graphical interface and kept from direct
access to text documents when using a visual editor, syntactic violations
are physically impossible under normal situations. Nevertheless, this does
not make a syntactically valid document being very semantically mistaken
any less possible. For example, a static analysis rule says that the
from
specii cation and the
to
specii cation of an
assign
activity must be of com-
patible types. Syntactically, there will be no way to prevent an implemen-
tation of the very opposite. Therefore, BPEL Designer enforces validations
whenever a process is updated and saved with coni rmation. Immediate
feedbacks will be made available in the form of error, warning, or info
messages populated in the
problem
view window if any violation has been
caught. Line numbers of faulty dei nitions in the process document will be
given to locate the sources of violation. Users should then consider the
i xes before continuing.
Va l idat ion

Search WWH ::

Custom Search