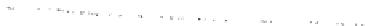Information Technology Reference
In-Depth Information
Fig. 5.19
The results of the
simulation research of the
system for recognition of
intruders in the system,
a
—the number of normal
agents,
b
—the number of
intruder agents loading the
resource
A
with the
probability 0
120
a
100
b
80
60
75, and the
resource
B
with the
probability 0
.
25
.
40
20
0
0
50
100
150
200
250
300
350
T
B
with the probability
p
i
B
=
25. In this case, we may also observe a decrease in
the number of the agents-intruders, but the process of identification and elimination
proceeds slower than in the first case.
A comparison between the development of eliminating the agents-intruders in the
former and the latter case is presented in Fig.
5.20
.
In both systems there are cases of false identification of intruders. It results from
the fact that the normal agent is perceived as an intruder and eliminated from the
system. However, in neither of the cases the number of eliminated normal agents is
significant (a few percent).
In the examples of the operation of the system some delay may be observed at the
start of eliminating the intruders. The time is used by the normal agents for preparing
0
,
70
a
60
50
40
30
20
10
c
b
0
0
100
200
300
400
500
600
700
800
T
Fig. 5.20
The results of the simulation research of the system for recognition of intruders in the
system,
a
—the number of normal agents;
b
—the number of intruder agents loading the resources
with the probabilities
p
i
A
=
p
i
B
=
1
.
0
,
0;
c
—the number of intruder agents loading the resources
with the probabilities
p
i
A
=
p
i
B
=
0
.
75
,
0
.
25