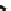Information Technology Reference
In-Depth Information
the recognition of atypical situations together with an attempt to react to perceived
threats. Let us consider a system consisting of two populations of agents and two
resources
A
and
B
existing in the environment. One population of agents consists of
so-called “normal” agents that load regularly the resources, loading certain amount
of one chosen resource, chosen randomly with certain probability. Normal agents use
the resource
A
with the probability
p
i
A
=
0
.
5 and the resource
B
with the probability
p
B
=
5.
The other population of agents consist of a certain number of intruder agents which
are characterized by the fact that the probability of loading the resource
A
as well as
the resource
B
is different from that of normal agents. In the system we study, the
population of intruder agents constitutes 12
0
.
5 % of the population of normal agents
and both populations appear at the moment
T
.
0.
Two cases of the operation of the system were considered:
=
1. The system in which agents-intruders only load the resource
A
(i.e., the resource
A
with the probability
p
i
A
=
0, and the resource
B
with the probability
p
i
B
=
0).
2. The system in which agents-intruders load the resource
A
with the probability
p
i
A
=
1
.
75, and the resource
B
with the probability
p
i
B
=
0
.
0
.
25).
The normal agents using, as described above, the models of behaviour based on
their own behaviour assess the behaviour of other agents and try to identify the
intruders and then remove them from the system. As a result of the appropriate
operation of the system, the number of the agents-intruders should drop, and the
number of normal agents should remain unchanged.
In Fig.
5.18
, the results of the first system are presented in which the agents-
intruders load only the resource
A
. We may observe a decrease in the number of the
agents-intruders up to their total disappearance in the system.
In Fig.
5.19
the results of the operation of the system are presented in which the
agents-intruders load the resource
A
with the probability
p
i
A
=
0
.
75 and the resource
120
a
100
80
60
b
40
20
0
0
5
10
15
20
25
30
35
T
Fig. 5.18
The results of the simulation research of the system for recognition of intruders in the sys-
tem,
a
—the number of normal agents,
b
—the number of intruder agents loading only the resource
A