Database Reference
In-Depth Information
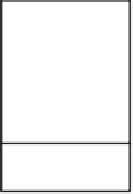
Linux Red Hat
Solaris 10
XP
Vista
OS X
VM1
VM2
VM3
VM4
VM4
Hypervisor or VMM
Hardware (e.g., a single desktop computer or the cloud)
FIGURE 16.3
Mixed-OS environment offered by system virtualization.
Moreover, traces of executions and dumps of machine states at points of interests
can be taken at the VM level, an action that cannot be performed on native systems.
Lastly, system execution can be replayed on VMs from some saved state for analyz-
ing system behavior under various scenarios. Indeed, the complete state of a VM
can be saved, cloned, encrypted, moved, and/or restored again, actions that are not
so easy to do with physical machines [15]. As such, it has become quite common for
OS researchers to conduct most of their experiments using VMs rather than native
hardware platforms [55].
16.2 LIMITATIONS OF GENERAL-PURPOSE OPERATING SYSTEMS
The operating system (OS) binds all hardware resources to a single entity, which is
the OS. This limits the flexibility of the system, not only in terms of applications
that can run concurrently and share resources but also in terms of isolation. Isolation
is crucial in cloud computing with many users sharing the cloud infrastructure. A
system is said to provide full isolation when it supports a combination of
fault isola-
tion
,
resource isolation
, and
security isolation
[56]. Fault isolation reflects the ability
to limit a buggy program from affecting another program. Complete fault isolation
requires no sharing of code or data. Resource isolation corresponds to the ability of
enforcing/controlling resource usages of programs. This requires careful allocation
and scheduling of resources. Lastly, security isolation refers to the extent at which
accesses to logical objects or information (e.g., files, memory addresses, and port
numbers) are limited. Security isolation promotes safety where one application can-
not reveal information (e.g., names of files or process IDs) to any other application.
General-purpose OSs provide a weak form of isolation (only the process abstraction)
and not full isolation.
On the other hand, virtualization relaxes physical constraints and enables opti-
mized system flexibility and isolation. Hypervisors allow running multiple OSs
side-by-side, yet provide full isolation (i.e., security, resource, and failure isolations).
To mention a few, hypervisors can effectively authorize and multiplex accesses to











Search WWH ::

Custom Search