Database Reference
In-Depth Information
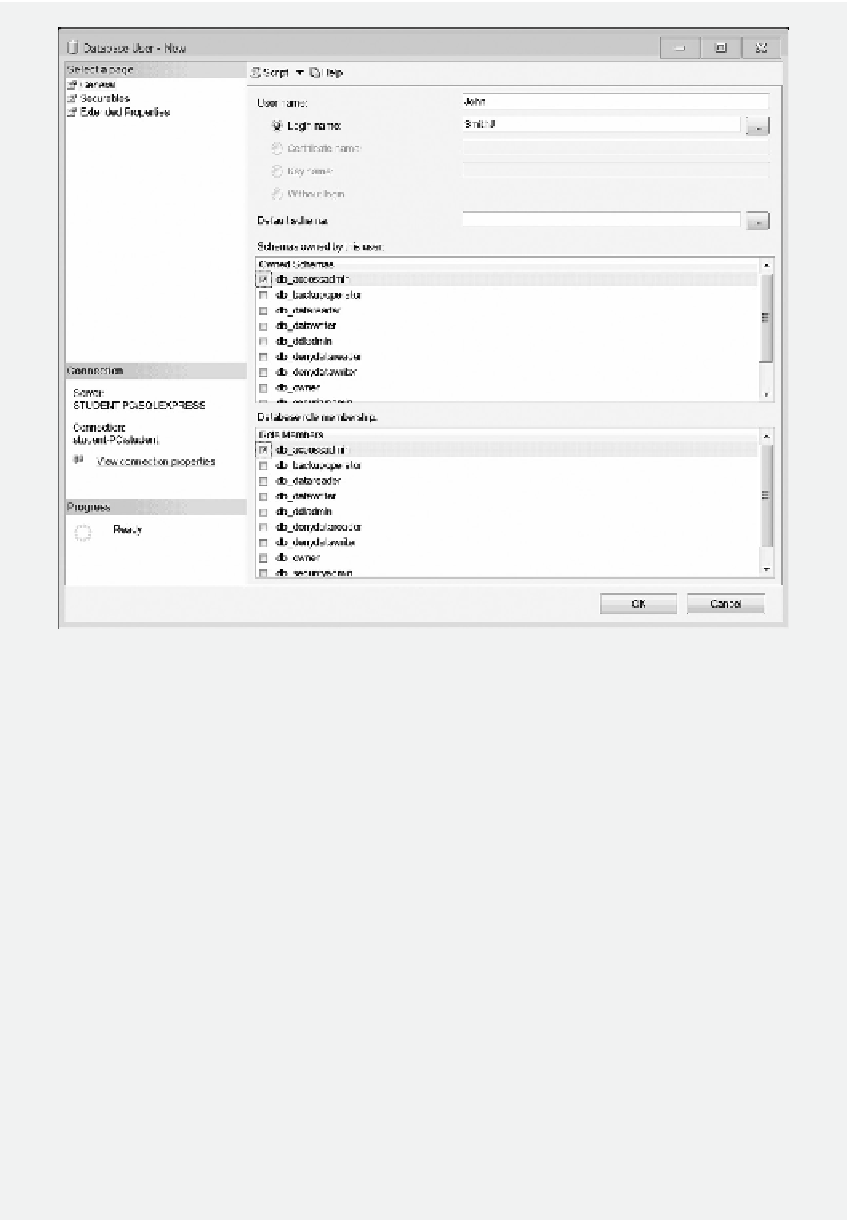
Figure 1.12
Database user.
Security
: With Security, you can conigure database security measures for data-
bases. he main security components are Users, Roles, Schemas, and Symmetric
Keys.
Users
: he Users object deines users in a database. It is used to create user accounts. A
user account is created to identify each individual user. A user can access his/her account
with his/her user name and password. After logging on to a database, the user can access
database objects with properly assigned ownership and permissions. You can grant and
modify permissions on objects in a database for users with this component. he user con-
iguration for a new user is shown in Figure 1.12.
Roles
: he Roles object allows you to group users with the same set of permissions.
Roles can be used to simplify administrative tasks. For example, when modifying
permissions, instead of changing the permissions for each individual user, you can
modify the permissions for the role. Once the role's permissions are changed, the per-
missions for all the users with the same role will be modiied automatically. When a
group of users perform the same kind of job, you should assign these users to the same
role and then conigure the same set of permissions to the role. Figure 1.13 shows the
coniguration of a role.