Information Technology Reference
In-Depth Information
DoT
j3
G'
G
'
DoT
j4
DoT
ji
DoT
1i
DoT
j5
G''
G''
G'''
DoT
2i
G'''
G
i
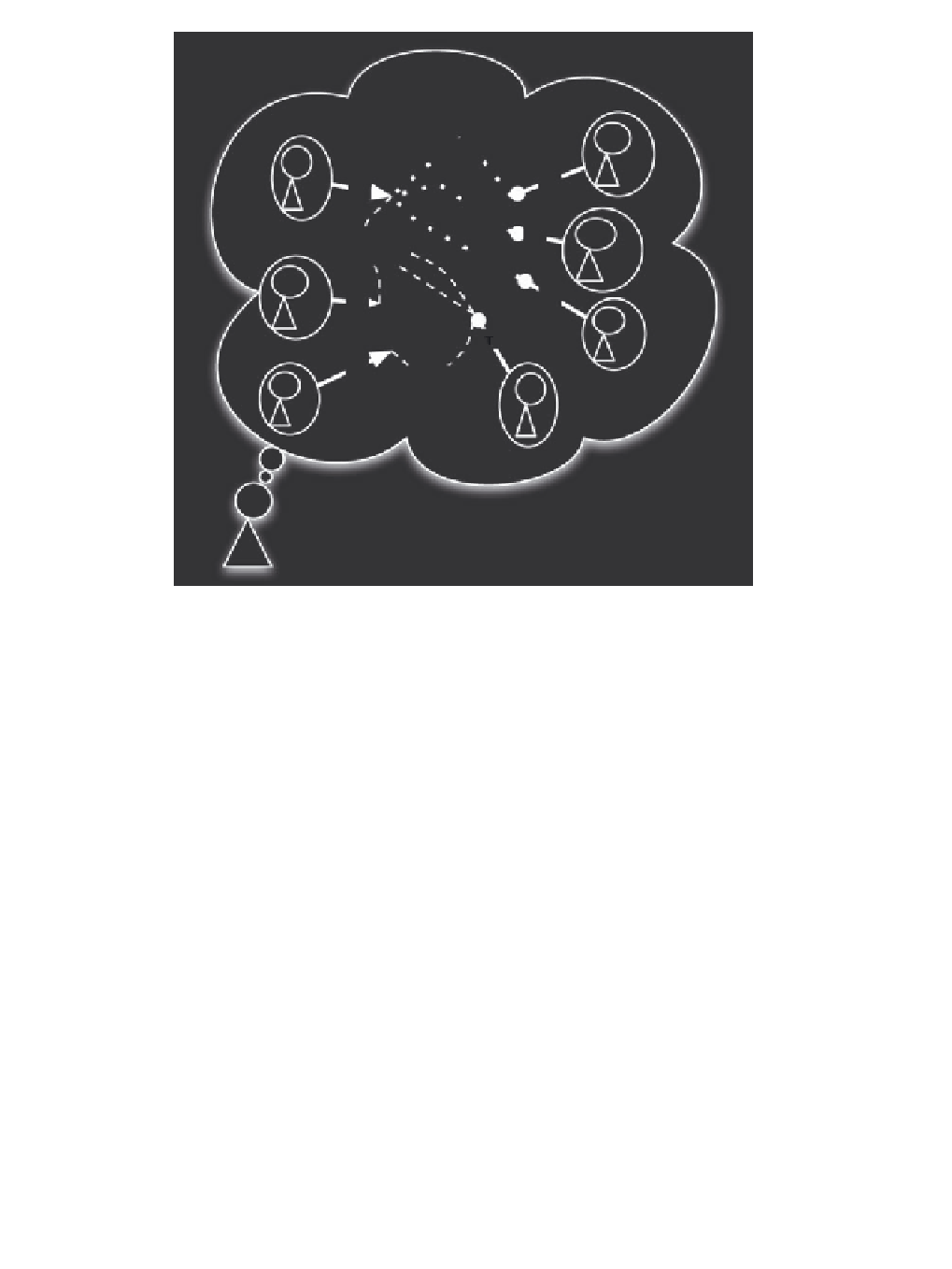
Figure 10.9
Example of positive (
Ag
j
,
Ag
1
,
Ag
2
) and negative (
Ag
3
,
Ag
4
,
Ag
5
) contributors to
Ag
i
's
capital of trust (in
Ag
i
's mind)
that can realize and achieve the same task (with a trust value comparable with the one of
Ag
i
)
to whom
Ag
j
can delegate the task
τ
k
(see Figure 10.9).
We say that there are two
comparable trust values
when the difference between them is
in a range under a given threshold that could be considered meaningless with respect to the
achievement of the task.
In Figure 10.9,
Ag
1
and
Ag
2
strengthen the trust capital of
Ag
i
(they are competitors with
Ag
j
about the task
); while
Ag
3
,
Ag
4
and
Ag
5
weaken the trust capital of
Ag
i
because they
are competitors with
Ag
i
in offering (at the same trustworthy value) the task
τ
.Asshownin
Figure 10.9, it is possible that
Ag
i
believes in potential competitors (jeopardizing his trust
capital), but they are not really competitors because there are no links with his potential clients/
delegating (see
Ag
3
,
Ag
4
and
Ag
5
that are not linked with
Ag
1
and
Ag
2
but only with
Ag
j
).
Of course, we can analogously introduce the
Objective Usable Trust Capital
of
Ag
i
∈
τ
Agt
τ
k
as:
about a potential delegable task
l
DoT
(
Ag
j
,
Ag
i
,τ
k
)
OUTC
(
Ag
i
,τ
k
)
=
(10.12)
+
1
p
kj
j
=
1






Search WWH ::

Custom Search