Information Technology Reference
In-Depth Information
Table 6.5
Pseudo-Transitivity: Combining the Degrees of Trust
DoT
ZYτ
> σ
2
DoT
Z Yτ
σ
2
DoT
X Z (ev)τ
> σ
1
X trusts Y as for
τ
X does not trust
Y as for τ
X trusts Y OR
X does not trust
Y as for τ
DoT
X Z (ev)τ
σ
1
X trusts Y OR
X does not trust
Y as for τ
mainly due both to the utility and diffusion of the practice itself: it can be a simple conformity
feeling and imitation; or it can be an explicit cognitive evaluation such as: 'since everybody
does it, it should be quite safe (apparently they do not incur systematic damages)'. If everybody
violates traffic rules, I feel encouraged to violate them too.
More formally, we have:
given
S
we are considering the set of agents belonging to the commu-
nity as reference for trust diffusion.
=
{
s
1
,. ., s
n
}
(
DoT
Z
n
Y
τ
>σ
n
)) then
if Bel (
X
(
DoT
ZY
τ
>σ
2
)
∩
(
DoT
Z'Y
τ
>σ
3
)
∩
...
.
∩
DoT
XY
τ
>σ
1
.
Z
Z
τ
τ
Trust on
Trust on
τ
τ
Trust on
Trust on
X
X
Y
Y
τ
τ
Trust on
Trust on
τ
Trust on
W
W
J
J
t
1
t
2
t
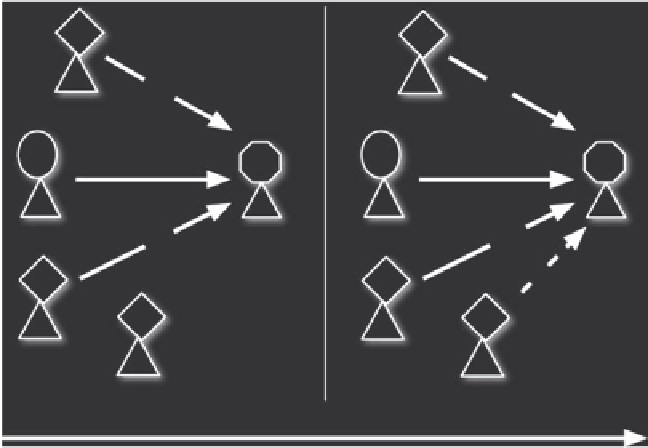
Figure 6.12
Trust Conformism





Search WWH ::

Custom Search