Database Reference
In-Depth Information
MariaDB Security
Bad things happen—accidentally and on purpose—and we want to protect our
MariaDB database against both. Threats come in many different forms and come
from many different places including—but not limited to—physical threats,
filesystem threats, network threats, and user threats.
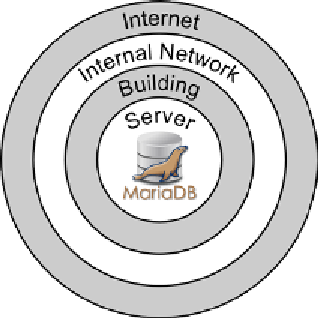
You can think of the data in your database as being at the center of a set of rings as
illustrated by the following diagram:
The outermost ring is the
Internet
. This is the outside world. If we are running a
business this is where our customers are. It's also where many attacks originate.
The next two rings are our
Internal Network
and the
Building
where our MariaDB
database server is located. Internal corporate networks can span several buildings,
but if we're a small business or a hobbyist the network might just be a single building
or even a room or two inside a building or house. We need to be careful of the
security on our internal network as we are on the external Internet, especially since
more attacks come from inside networks than from the outside world.