Information Technology Reference
In-Depth Information
host, the host is likely to have access to all the data and code carried by the agent. If by chance a host
is malicious and abuses the code or data of an agent, the privacy and secrecy of the agent and its owner
would be at risk.
Seven types of attack by malicious hosts (Defago, Schiper, & Sergent, 1998) can be identified:
1. Spying out and manipulation of code;
2. Spying out and manipulation of data;
3. Spying out and manipulation of control flow;
4. Incorrect execution of code;
5. Masquerading of the host;
6. Spying out and manipulation of interaction with other agents; and
7. Returning wrong results of system calls to agents.
There are a number of solutions proposed to protect agents against malicious hosts (Chan et al., 1993),
which can be divided into three streams:
•
Establishing a closed network: Limiting the set of hosts among which agents travel such that agents
travel only to hosts that are trusted.
•
Agent tampering detection: Using specially designed state-appraisal functions to detect whether
agent states have been changed maliciously during its travel.
•
Agent tampering prevention: Hiding from hosts the data possessed by agents and the functions to be
computed by agents, by messing up code and data of agents, or using cryptographic techniques.
None of the proposed solutions solve the problem completely. They either limit the capabilities of
mobile agents, or are not restrictive enough. A better solution is being sought, and there is no general
methodology suggested to protect agents. In the mean time, developers of mobile agent systems have
to develop their own methodologies according to their own needs. Apart from attacks by malicious
hosts, it is also possible that an agent attacks another agent. However, this problem, when compared
with the problem of malicious hosts, is less important, because the actions of a (malicious) agent to
another agent can be effectively monitored and controlled by the host on which the agent runs, if the
host is not malicious.
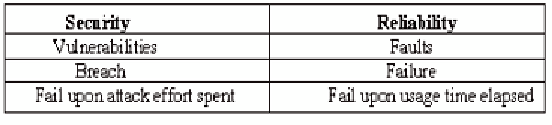
Table 2. Analogy between reliability and security
Search WWH ::

Custom Search