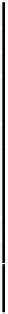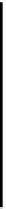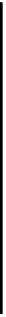Information Technology Reference
In-Depth Information
has been obtained from their relevant references (9, [32-40]). All algorithms are evaluated by
simulation implemented for USnet. Table 5 shows the complexity of the algorithms, where
V
is the set of network nodes,
D
is the set of destination nodes, and
S
represents the number of
MC nodes. Moreover, the number of un-overlapped working segments on a primary light-tree
is showed with
m
.
Table 3. Complexity of unicast protection algorithms
Protection algorithm
Complexity
Non-SRLG
NA
O(kN
3
)+kO(N
2
)
Pd-SPP
TS
O(NT)
(2 + D
2
)O(N
2
) + O(D
2
).
HCSPP
OHS
NA
SPAVT
O(│L│+│L│.log│N│)
&
O(│k
2
.│N│
8
│)
O(KN
2
W)
FT-ABR
(n(n-1))O(N
2
)
RSSP
Network coding
NA
LSA
NA
Table 4. Blocking probability (%) vs. traffic load (Erlang) for unicast protection
algorithms
Blocking probability (%) vs. traffic load
(Erlang)
30
Protection
Algorithm
W
N
40
60
80
100
Non-SRLG
NA
NA
NA
NA
NA
NA
NA
Pd-SPP
16
21
14
19
31
40.5
50.4
TS
16
16
0
0
5
11
20
HCSPP
8
21
2.53
2.642
11.123
23.542
32.365
OHS
4
12
15.2
18.5
22.3
26.5
34.5
SPAVT
NA
NA
NA
NA
NA
NA
NA
FT-ABR
8
14
0.5
1
5.2
8.4
10.2
RSSP
16
16
-----
0.55
1
10
35
Network coding
NA
NA
NA
NA
NA
NA
NA
LSA
8
24
0.1
1.5
2.5
4
5
Table 5. Complexity of multicast protection algorithms
Protection algorithm
Complexity
O(│D││V│
2
)
OPP-PRL
O(│D││V│
2
)
SLP-ARL
O(│V│
2
│D│
2
)
MPSP
O(│S││D││V│
2
)
SLPP
O(│V│
5
)
ASSP
O(│V││D│
2
+m│V│
2
)
SSPR
O(2(│D│+│D│
2
).│V│
2
)
SSMP